Overview
To integrate your Customer Portal with your corporate Azure AD you need to carry out the configuration steps as described in this section.
Note that these are done only once, typically by an admin user of your Customer Portal having access to your Azure AD.
|
We recommend considering using the SAML 2.0 protocol before using WS-Federation. See Configure Azure AD using SAML 2.0. |
Once you have carried out these steps users sign in to any cloud-based service directly via your Azure AD, as described at Signing in the Bizagi Cloud Portals and Applications.
Before you start
The Customer Portal and cloud-based services supports Azure AD using the WS-Federation protocol. The WS-Federation supported version is 1.0. Other versions are not supported. You need to consider before you start.
To have already users into the Customer Portal
When integrating any Identity Manager, you need to synchronize authorized accounts so they can access Bizagi 's cloud-based portals.
Synchronizing means importing or updating the account's primary identifiers. The Bizagi's account email must match with the attribute considered as the identifier in ADFS. See Create company users.
Bizagi does not store passwords when integrating an Identity Manager.
|
You cannot have two or more users with the same email, because it is considered as part of the primary identifier. |
Once you have verified in the Customer Portal that there has been at least an initial import of your users into Bizagi, you may proceed.
What you need to do
An outline describing the configuration needed to sign in with Azure AD considers these steps:
1.Register an authorized application in Azure AD.
2.Configure Azure AD in the Customer Portal.
Configuration
Follow the steps presented to integrate your Azure AD after you've created the company users:
1. Register an authorized application.
This step is done directly at your Azure portal by doing:
Sign in to Azure's portal at https://portal.azure.com.

Go into your Active Directory.
Click the Azure Active Directory option at the left panel to add a new application to it.
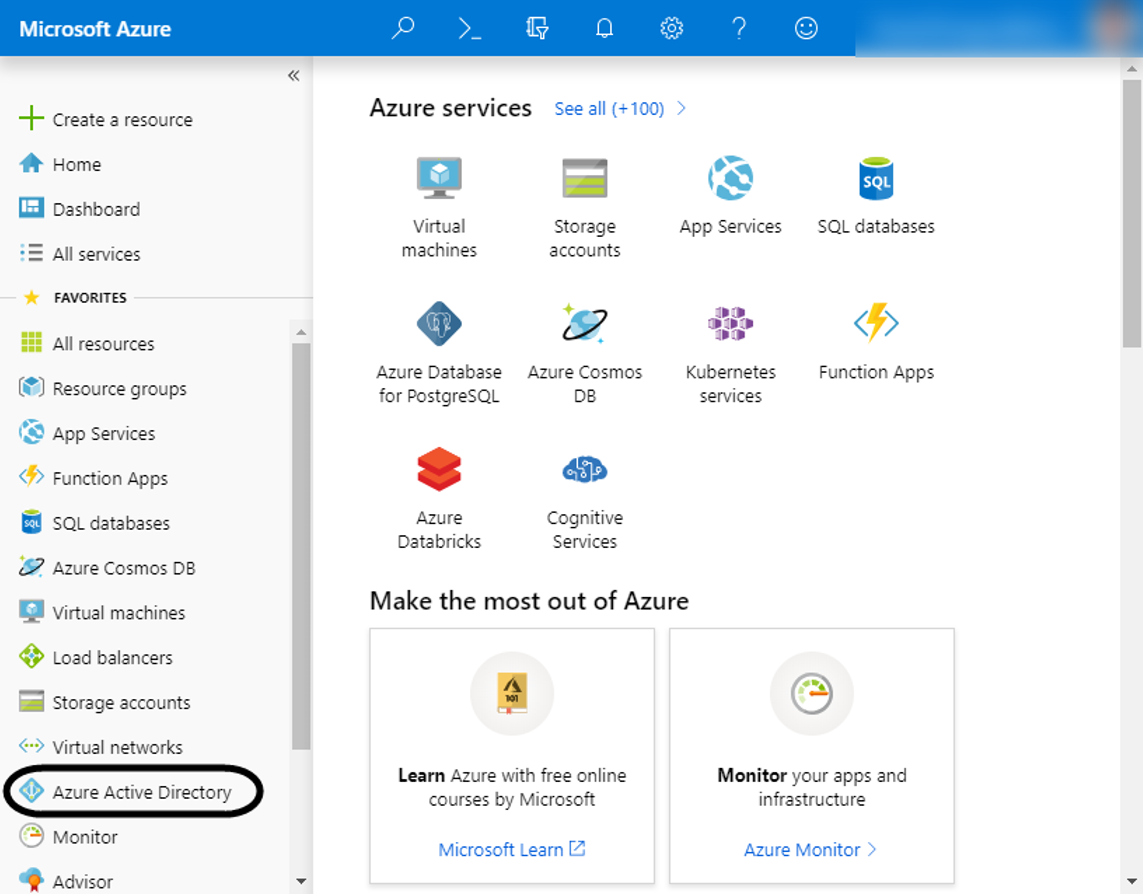
Add a new app.
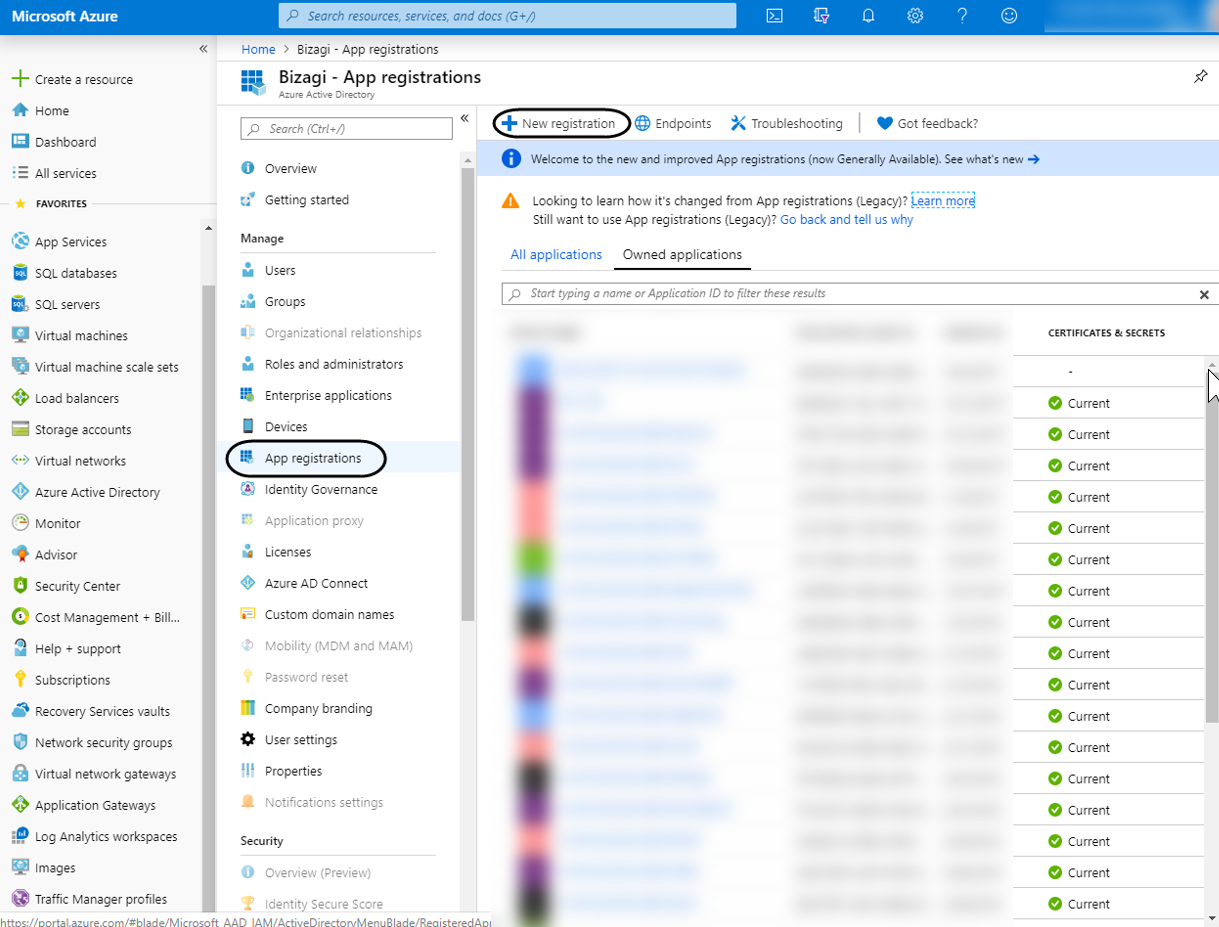
Click the App registrations option and click on New registration located in the ribbon.
Input the app's basic details:
Give this application a name (can be changed later), select a Supported account Type (Single-tenant Recommended) and set
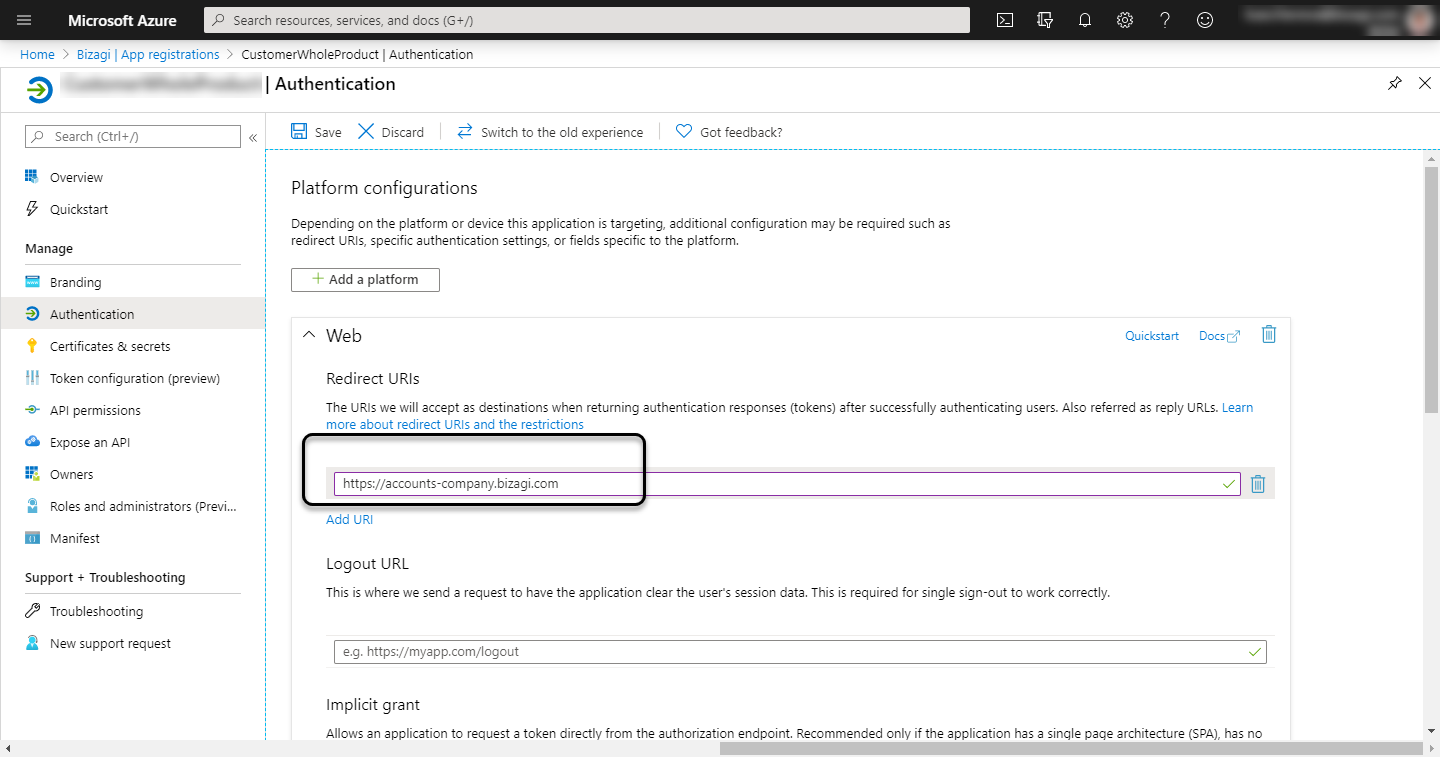
https://accounts-[your_company].bizagi.com
as Redirect URI. Web option must be selected.
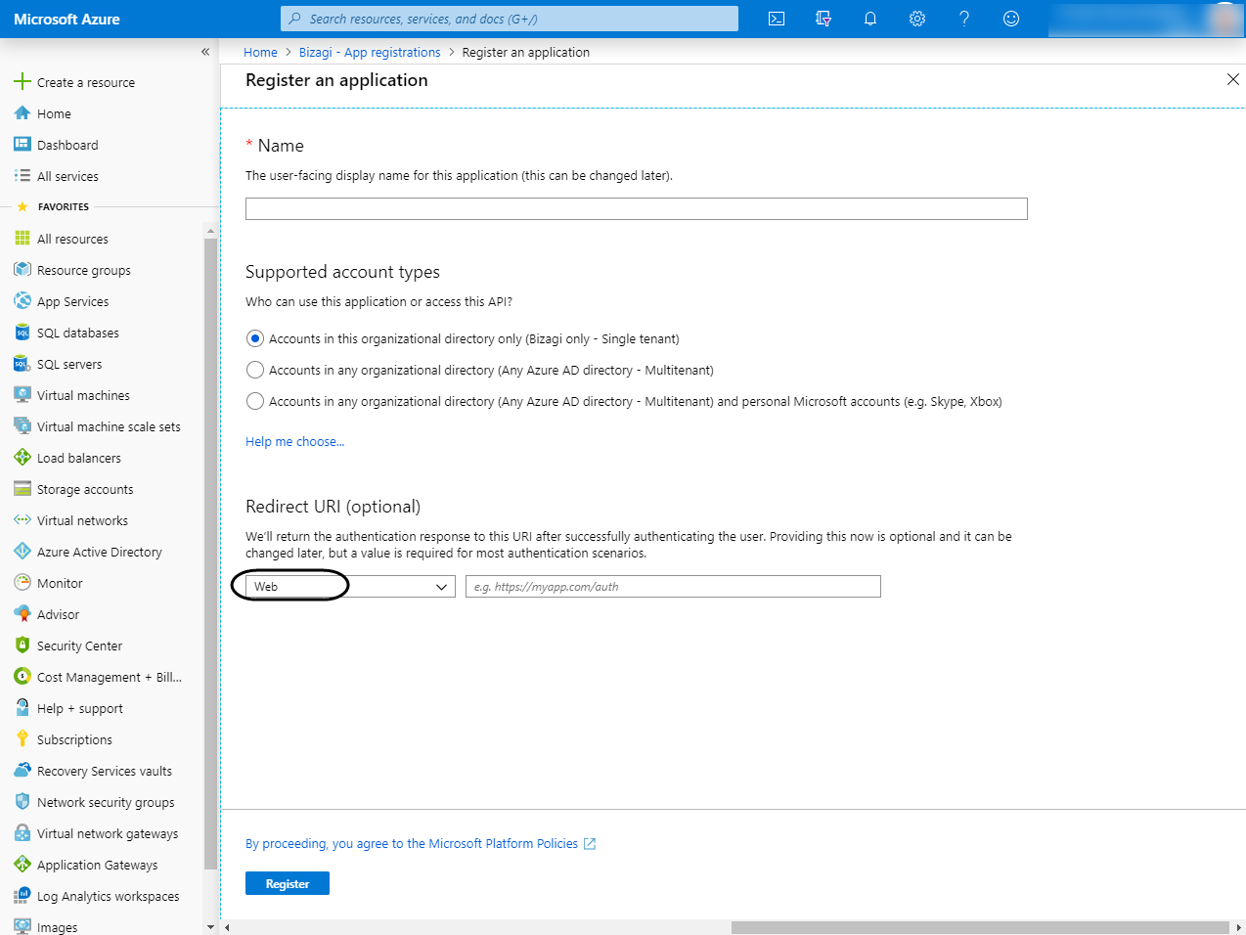
Click Register. The application might take several minutes to create your new application
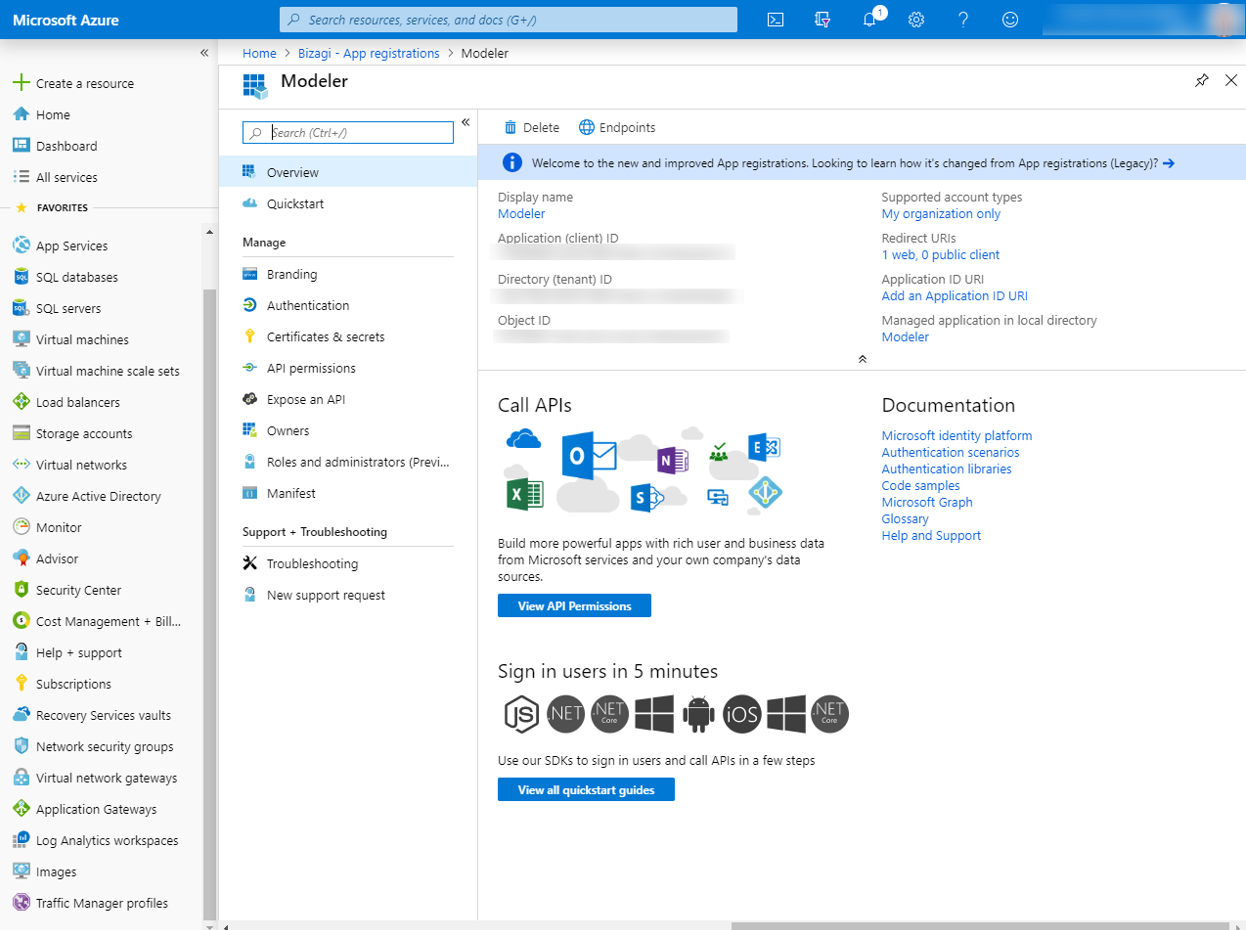
Make sure that the Redirect URI in the newly created app is ok, to do this, click the Redirect URI option of the newly added app.
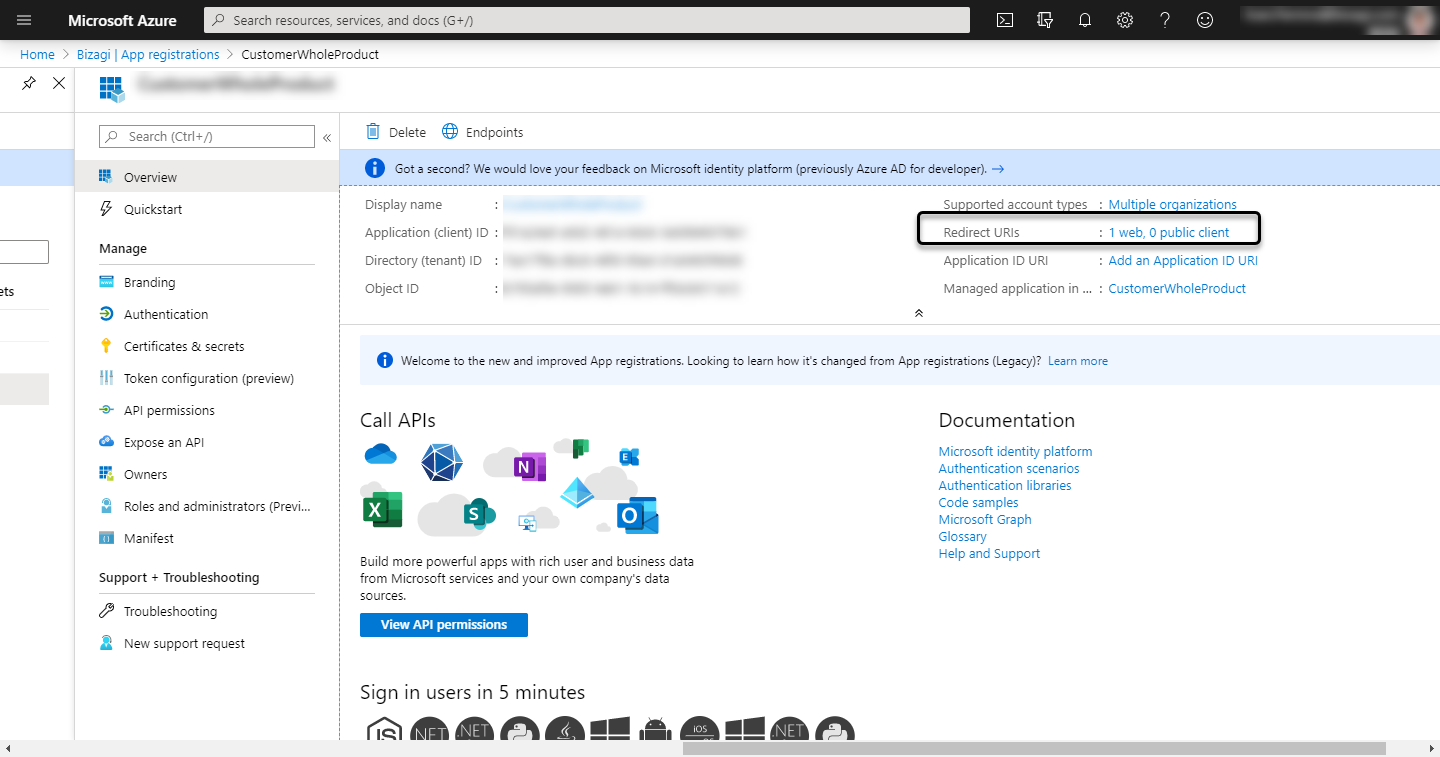
Make sure is the accounts URL:
Open the Expose API menu, click on Set Application ID URI
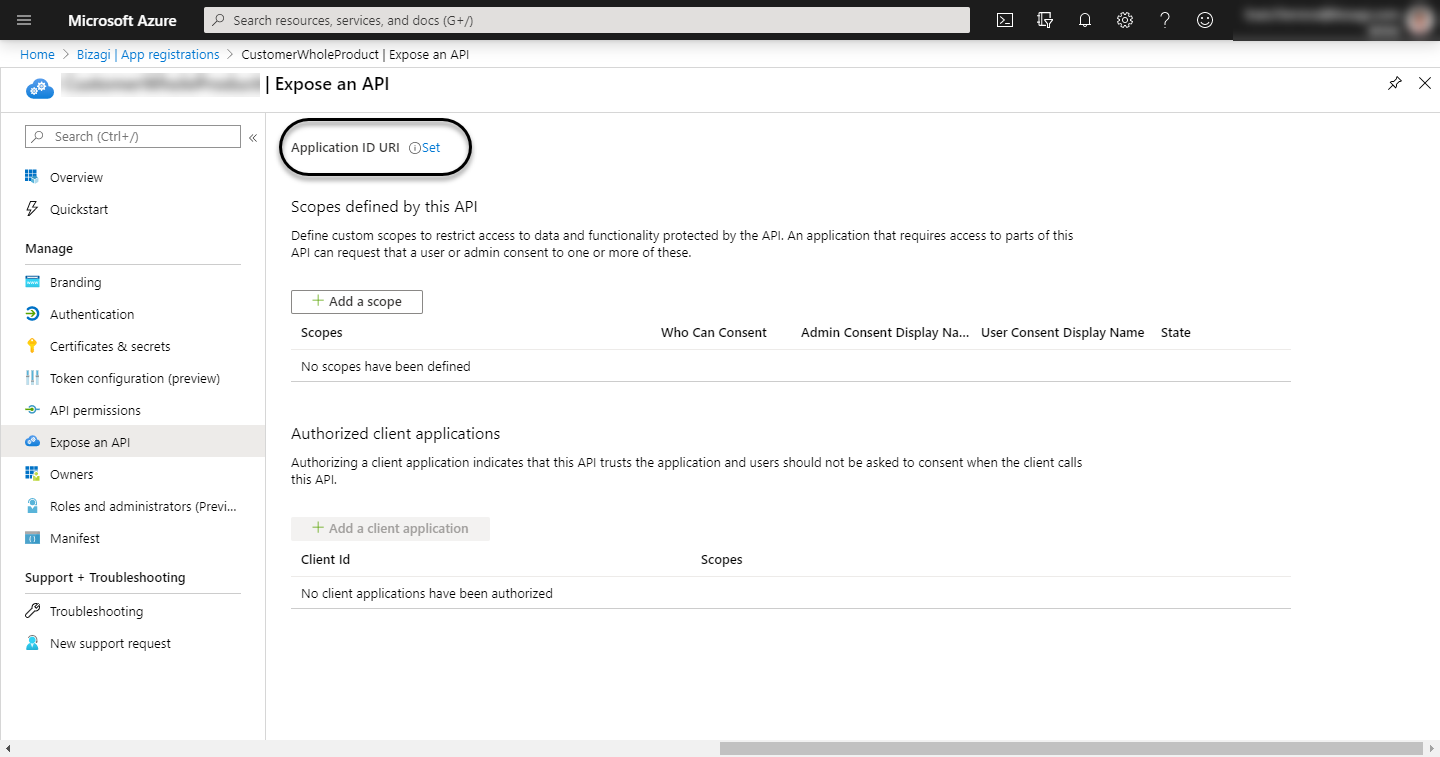
and leave the ID that Azure displays by default. Click Save without editing any value.
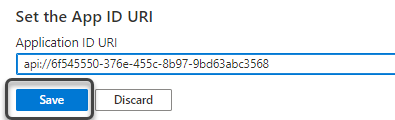
Click Save when done.
Add a new Scope and register the following information:
•Scope name: https://accounts-[your_company].bizagi.com
•Who can consent: Admins and users
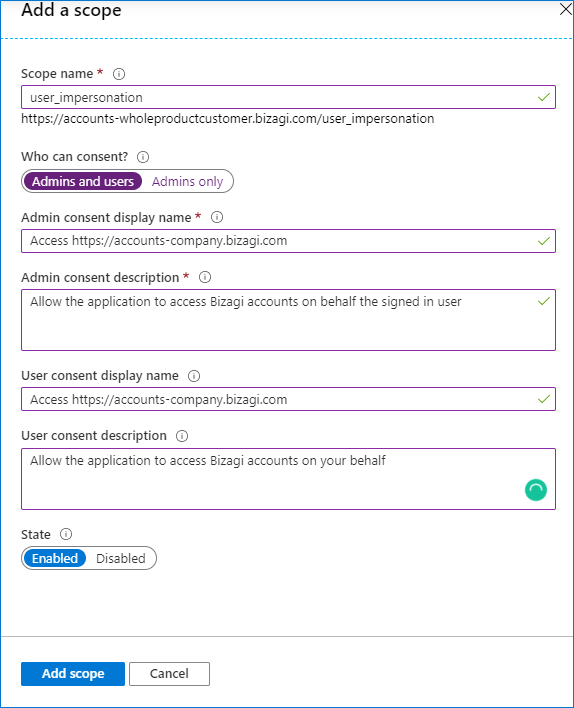
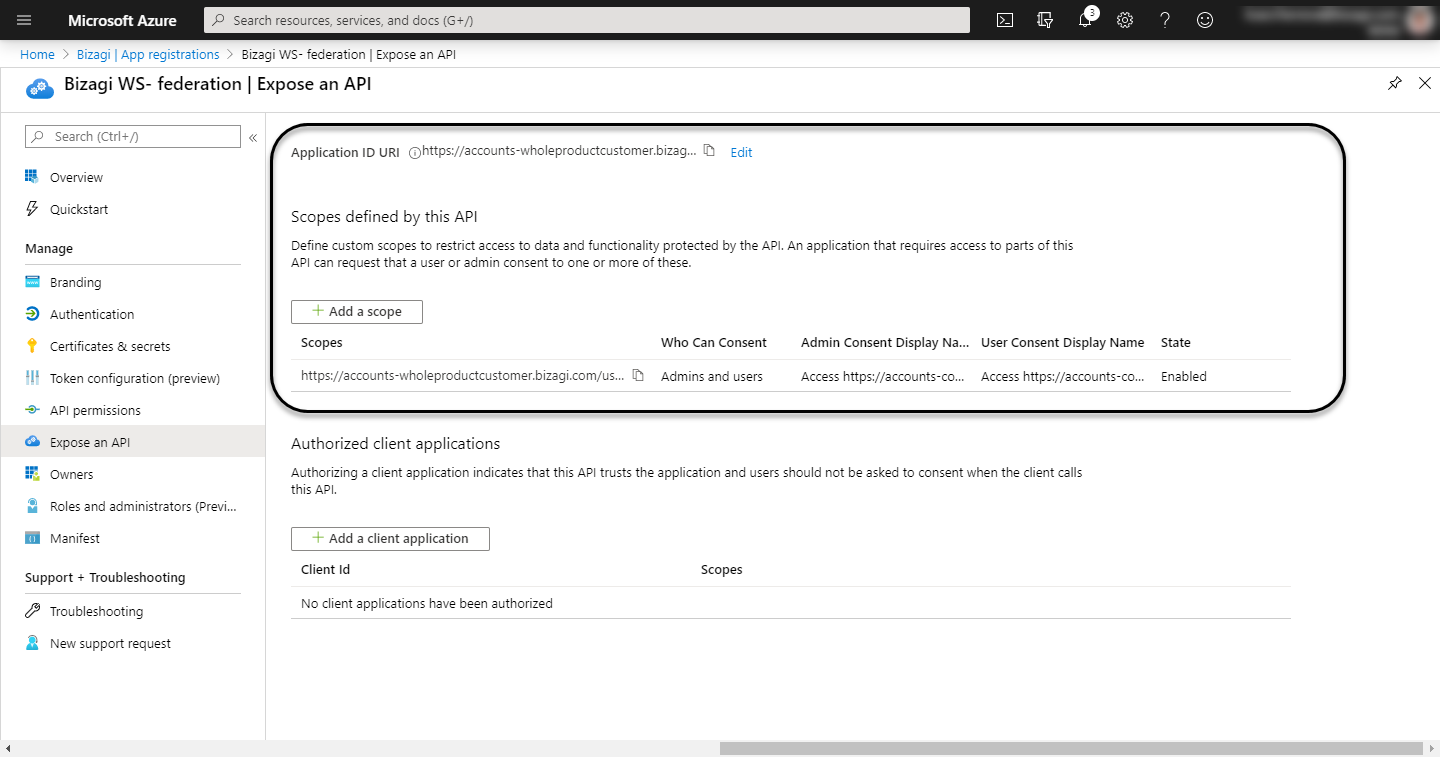
Add the scope.
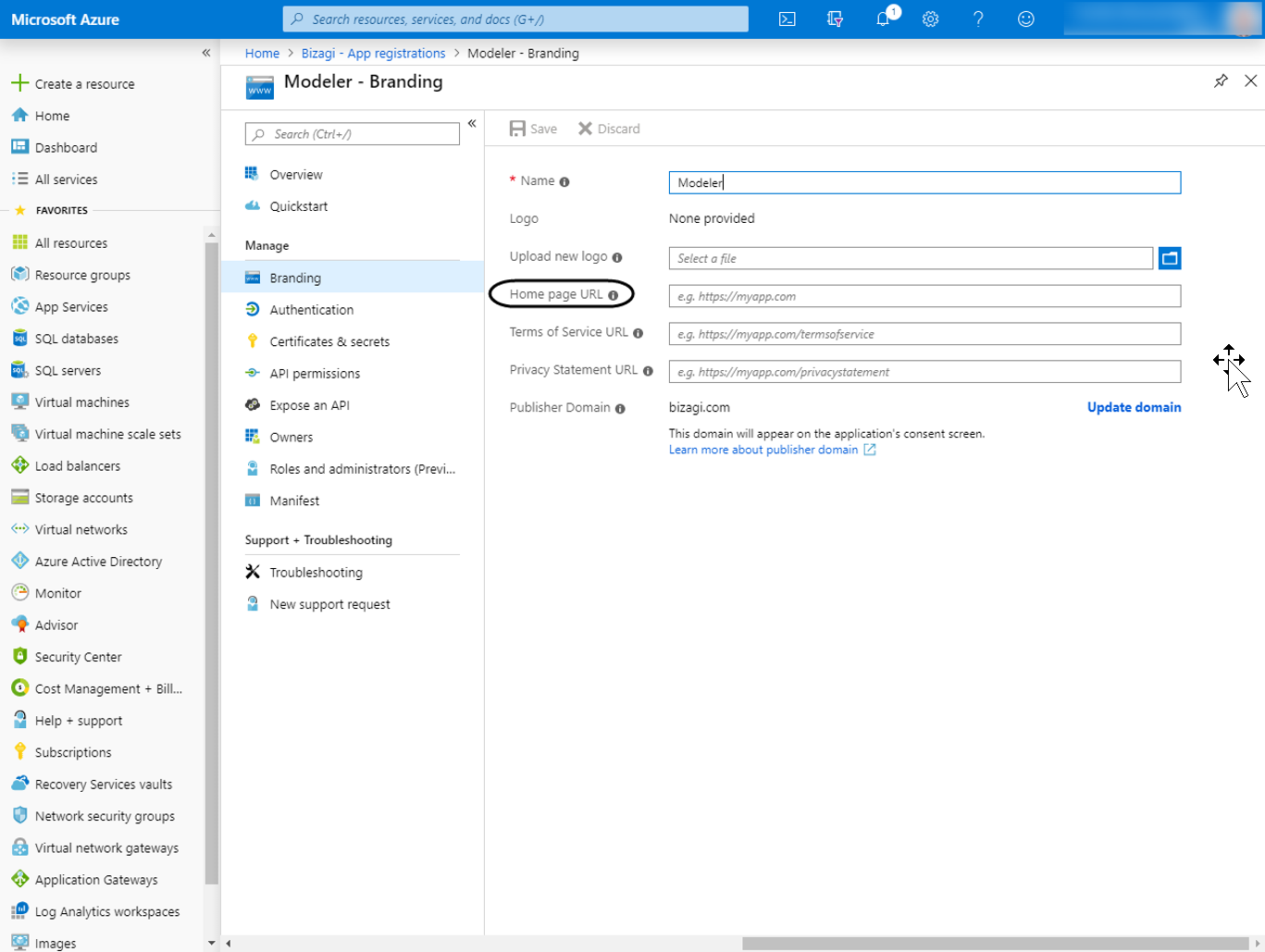
Set the Home page URL of the newly created app
To do this, go into the Branding option of the newly added app and set the Home page URL with https://accounts-[your_company].bizagi.com and click Save.
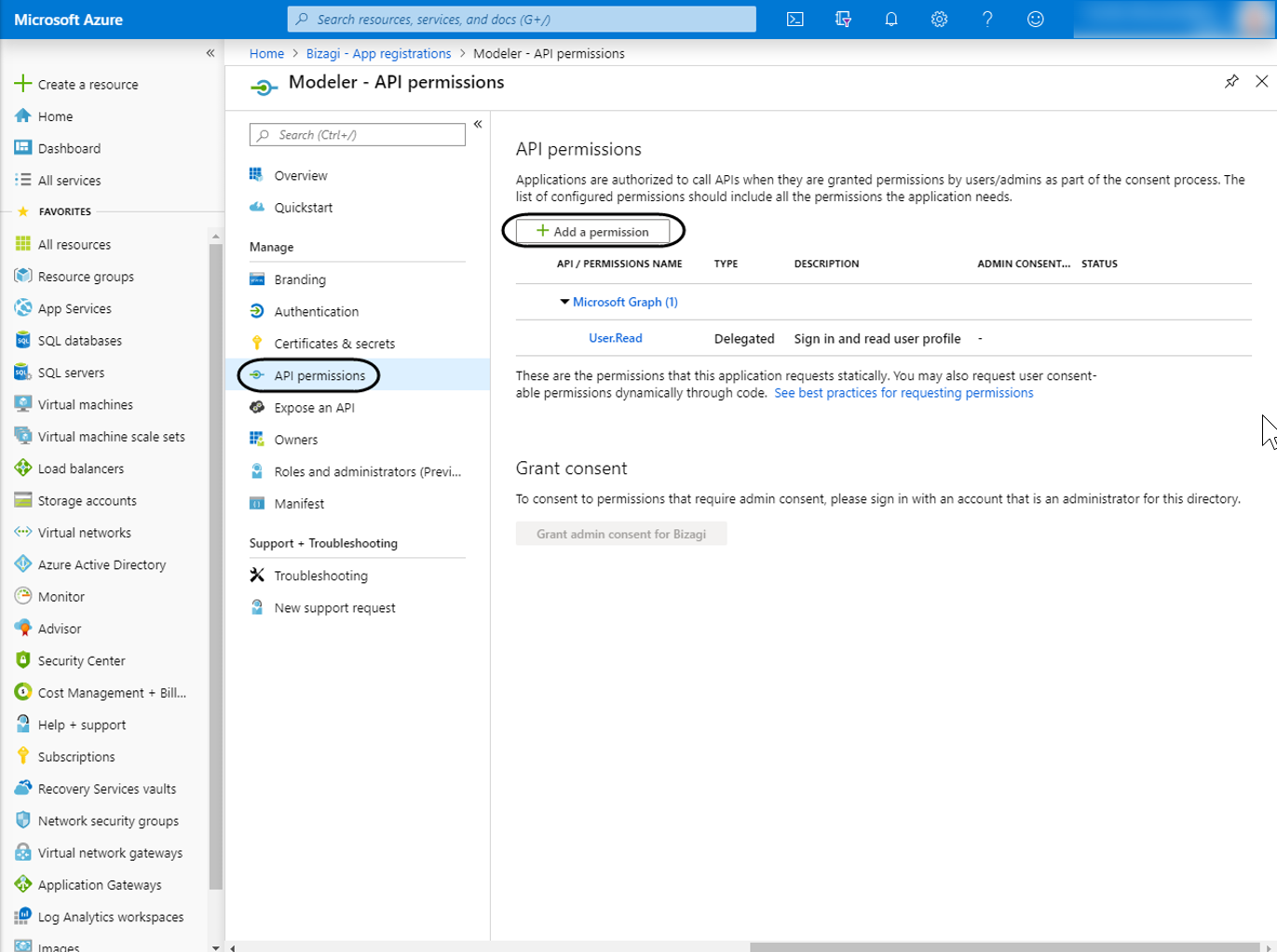
Set the appropriate permissions
To do this, go into the API permissions option of the newly added app and then, click Add permission.
Scroll Down until Supported legacy API and select Microsoft Graph.
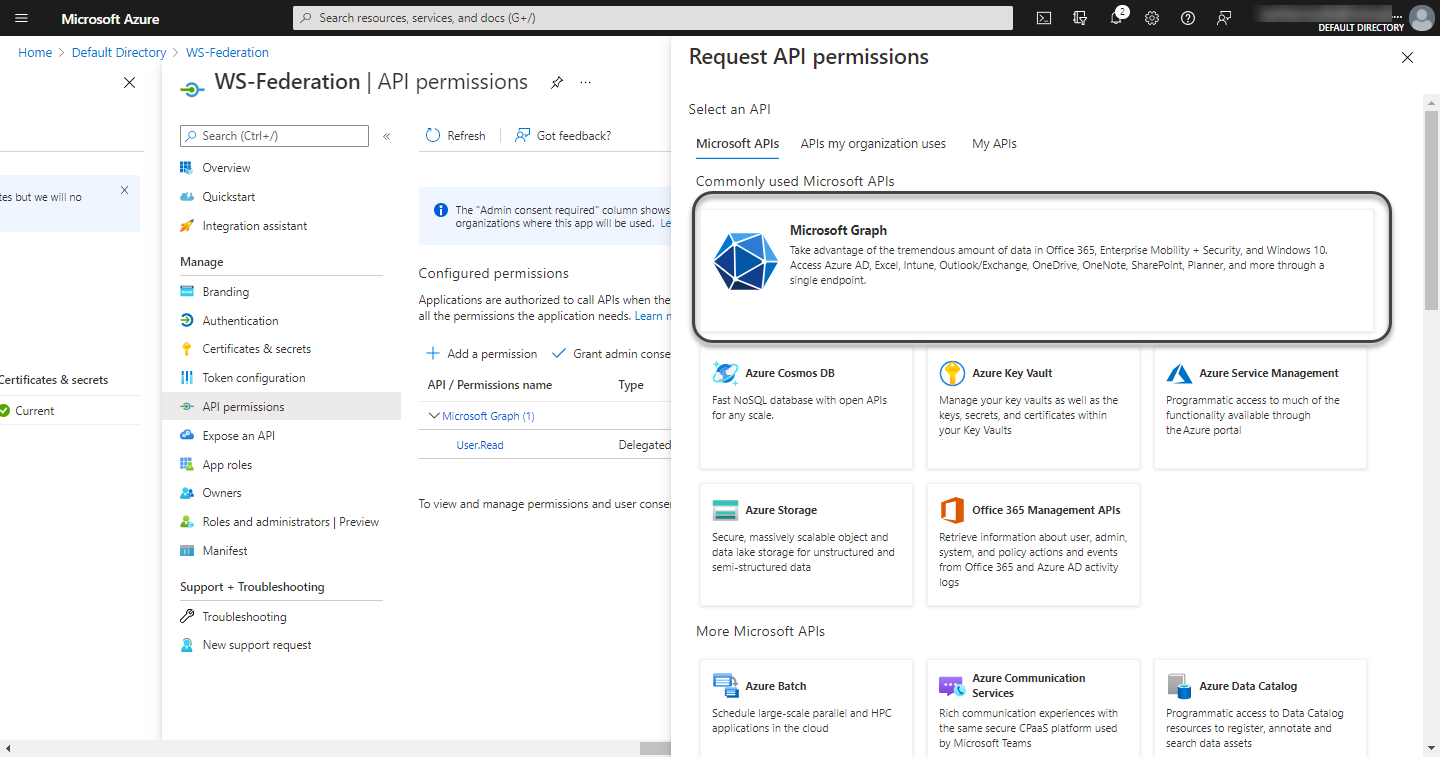
Select Delegated permissions and set it as is showed in the image:
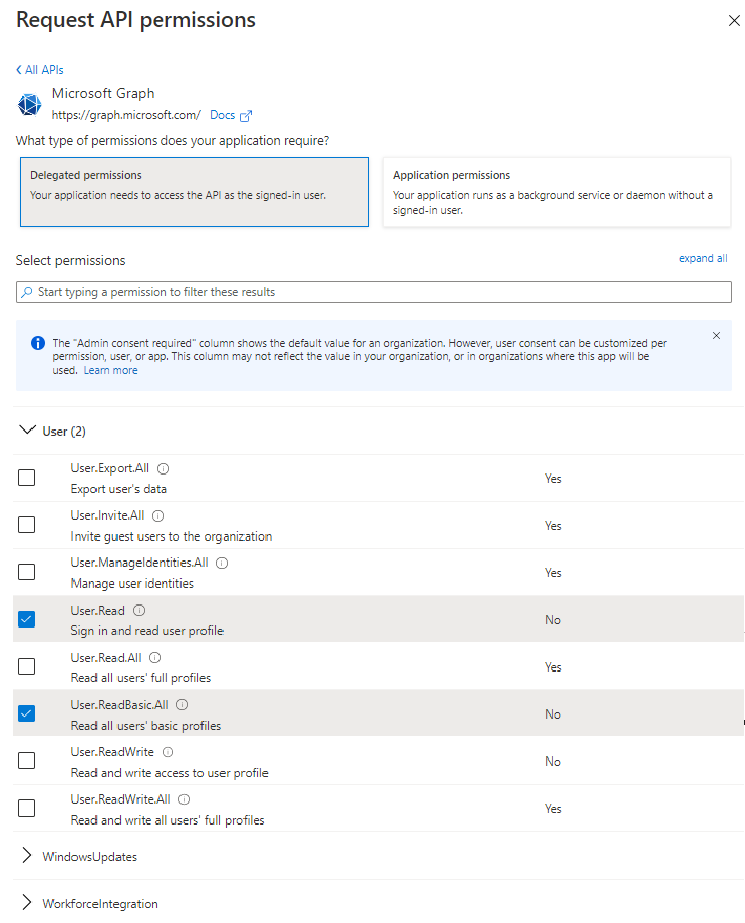
Click Add permissions to finish.
Open the Endpoints section of your application:
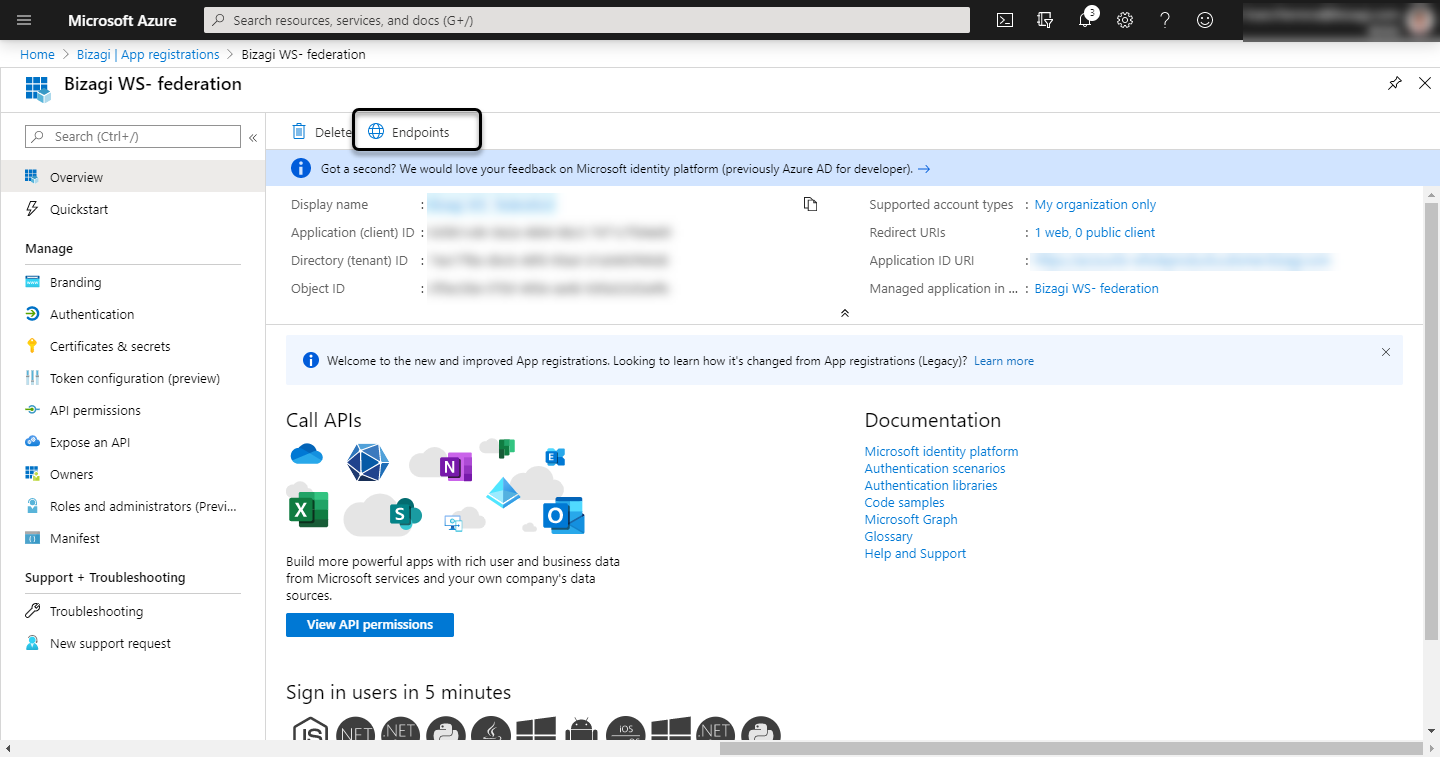
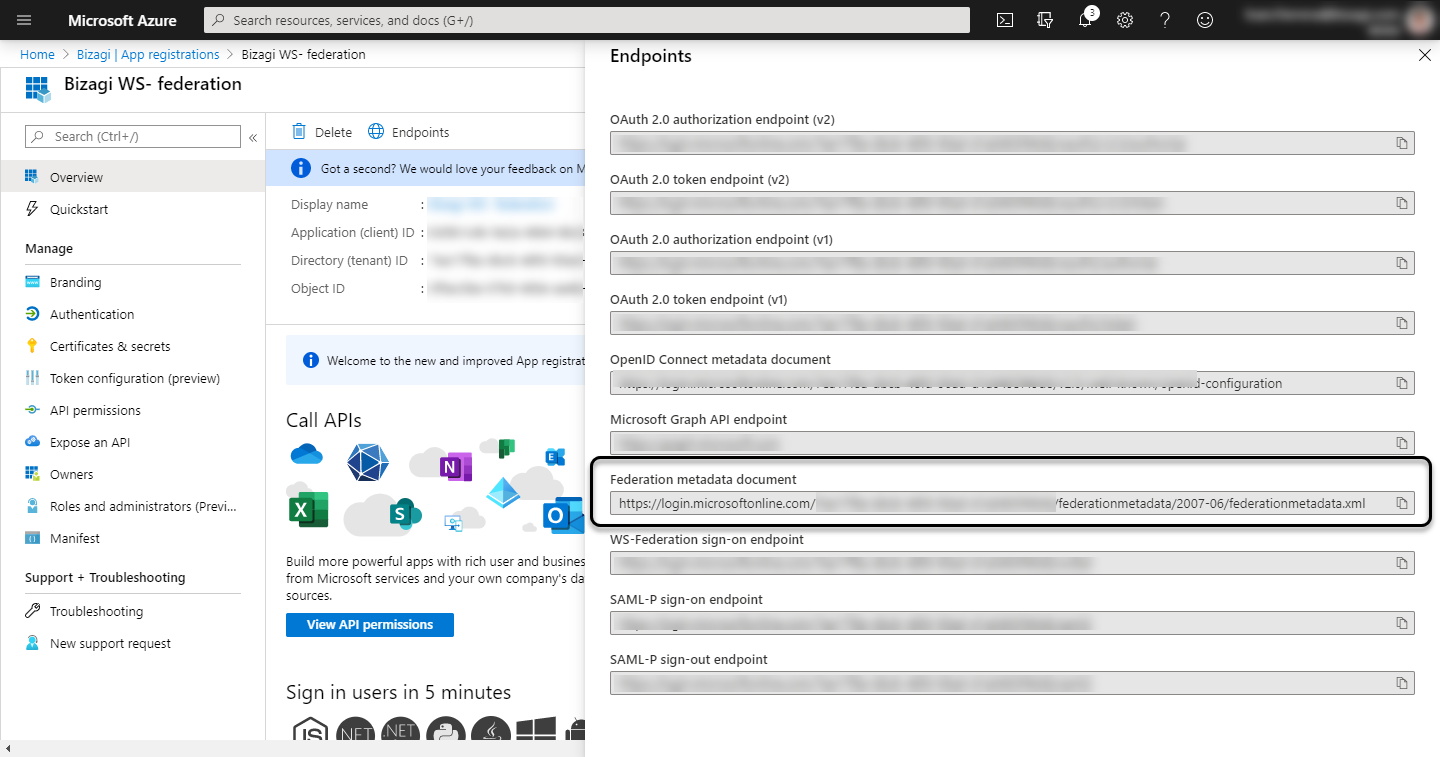
And copy the Federation metadata document:
2. Configure Azure AD in the Customer Portal
To configure Okta as your Customer Portal's Identity Provider, you need to access the Customer Portal as a company administrator, select the Settings Icon, open the Protocols menu, and click Add authenticator.
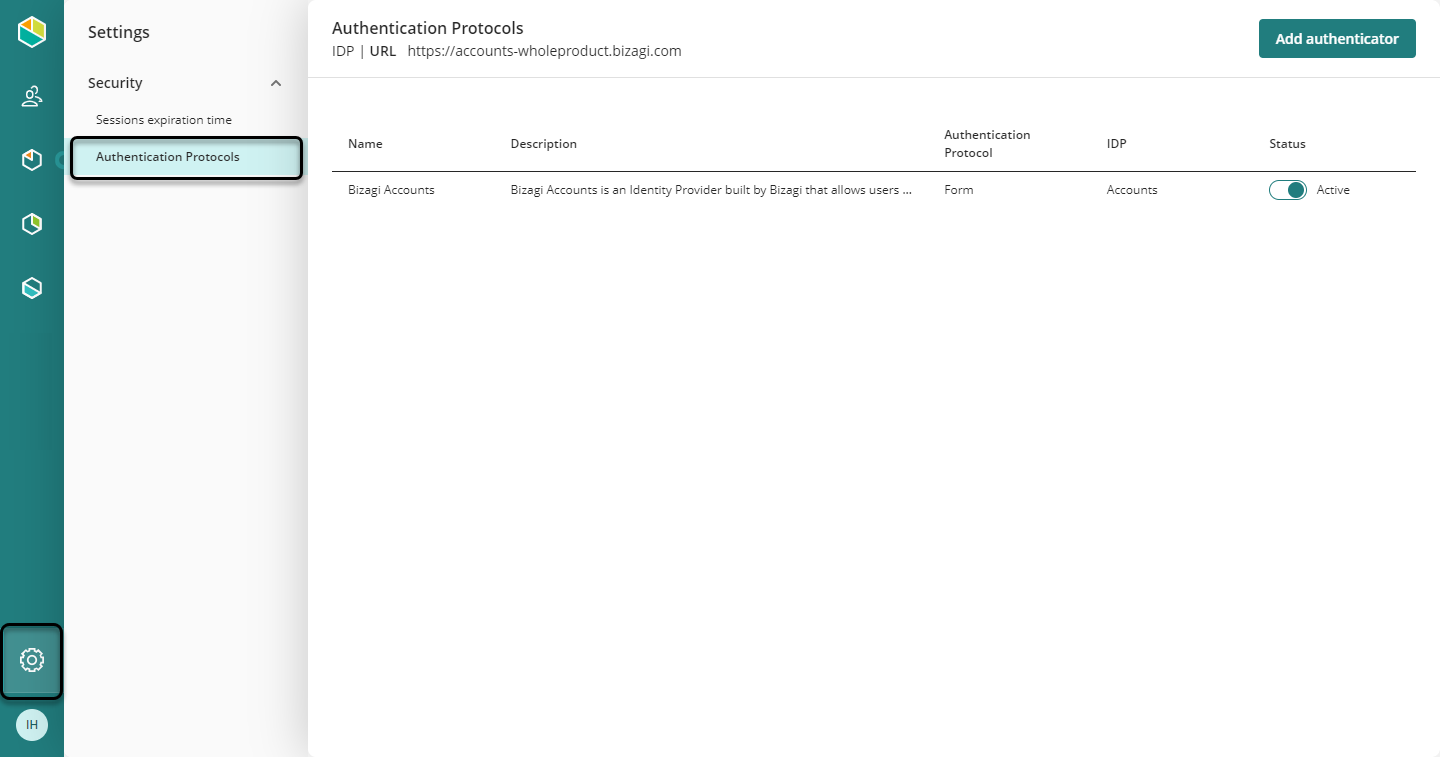
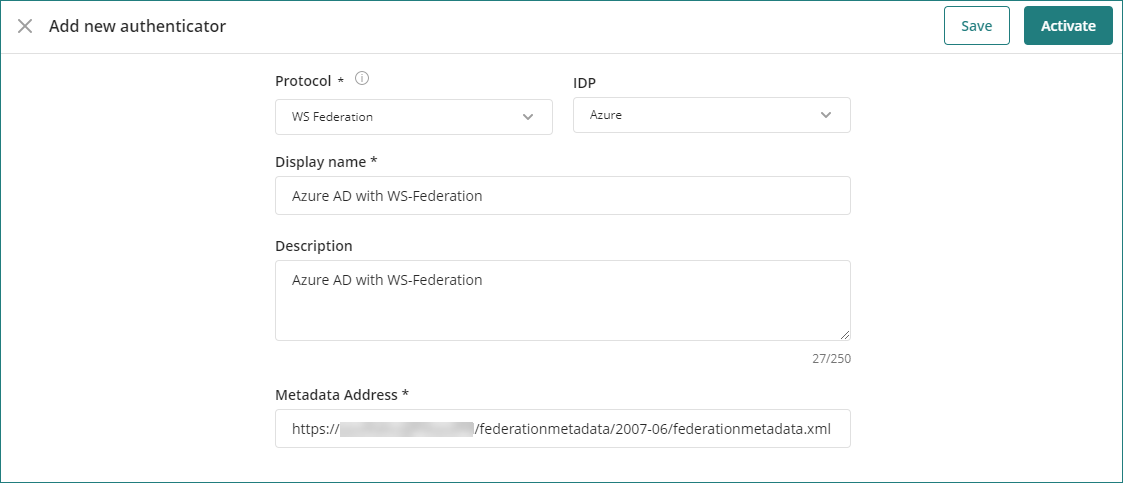
Select the Open ID connect option in the protocol drop-down list, and configure these settings:
•Display name: name of the authenticator displayed in the Customer Portal.
•Description: Brief description of the authenticator.
•Metadata Address: This is the ADFS federation metadata URL. This URL must be accessed via HTTPS while the authenticator is active. This URL must allow downloading the XML metadata file.
Define the domains
If you need to activate multiple authenticators, you can define the email domains associated with each authenticator. See Multiple authenticators for cloud-based portals.
Finally you need to activate the authenticator. Before activating the new authenticator, review carefully your configuration settings. Bizagi displays a warning message when activating the protocol.
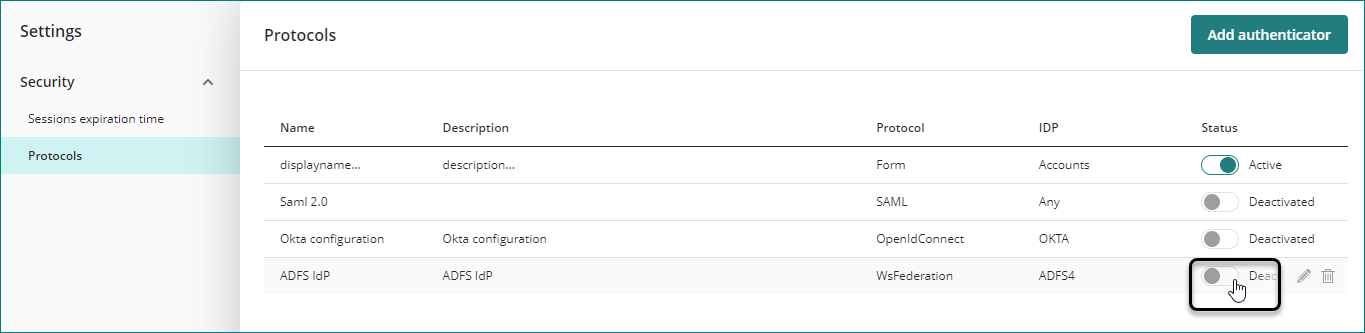
To test your configuration we recommend that all users log out and opening a new tab using incognito mode, or use a different browser. If the configuration with a new IdP fails, you can restore the authentication protocol.
Last Updated 7/18/2023 9:47:07 AM