Overview
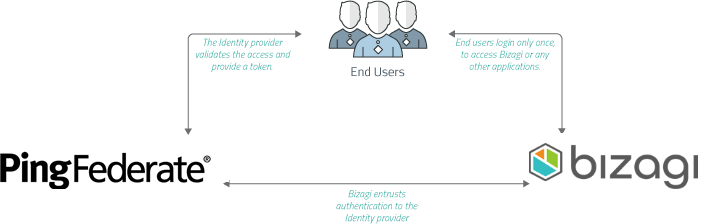
Bizagi supports integration with Identity and Access Management systems (i.e, Identity Managers or Identity Providers) which are SAML 2.0 compliant, such as PingFederate.
This section is a guide to the configuration needed, both in PingFederate and in Bizagi, to have an integrated authentication in Bizagi against PingFederate.
For SAML 2.0, both your Identity Provider and your Bizagi project must support HTTPS.
For introductory information about SAML 2.0, refer to Authentication via SAML.
|
If you plan on using an authentication method different than Bizagi and you are performing a deployment to an environment with no users on it (normally this would only be the case for a project's first deployment), follow these steps so that you can correctly configure your users and authentication without getting locked out of the Work Portal: 1.Perform the deployment with the authentication method set to Bizagi. This lets you access the Work Portal as the Admon user without providing any credentials. 2.Once in the Work Portal you can manually enter your users, or alternatively you can rely on the method of your choice to synchronize your users' information into the WFUser table (SOAP, Excel file, LDAP Synchronization, or performing a Data Synchronization procedure). 3.After having your users registered in the Work Portal, use the Management Console to set the authentication method to your preferred one.
If you plan on using LDAP authentication with periodic users synchronization, you may ignore the previous steps since you will only need to wait until the next synchronization happens for your users to be able to log into the Work Portal. |
1. Generate certificates to sign assertions (mandatory)
The following explains how to generate the security certificate from the Customer Portal:
|
You will need to be in charge of managing your installed certificates (keep track of its expiration date and other relevant maintenance aspects such as changes in your Identity Provider's endpoints). |
Create Authentication Certificates
You can generate security certificates for the Authentication Protocols within the Customer Portal. This feature allows you to create and configure a new certificate or upload an existing one in the Customer Portal. To setup the Single Sing On and access the Customer Portal, sign on to your account role as a Company Administrator. This user role can this user can create users in the company user's pool, and manage users in all the company subscriptions. For additional information about Managing Customer Portal and roles refer to:
To create a security certificate inside the Customer Portal follow these steps:
1.Select the Settings icon located in the left panel menu.
![]()
2.A panel expands from the left with all the security related topics. Select the Authentication certificates option.

3.Inside this section, there is a list of certificates with details like Name, Description, Expiration date, Owner and Creation date and its creation source. In the top right corner, select the Add certificate button.

4.The Add new authentication certificate window opens for you to create the new security certificate and you must fill out the five different required fields:
a.Display Name.
b.Description.
c.Either select the Generate (to create a new certificate) or Upload (to upload a existing certificate) option for the toggle button.
d.Expiration date.
e.Certificate password.
When you select the Generate option, set the Expiration date and assign a Certificate password. If you select the Upload option, you are required to upload digital certificates files in a PFX or a P12 format and then, select the type of algorithm to implement between SHA256 and SHA1. For last, enter the password from the certificate.
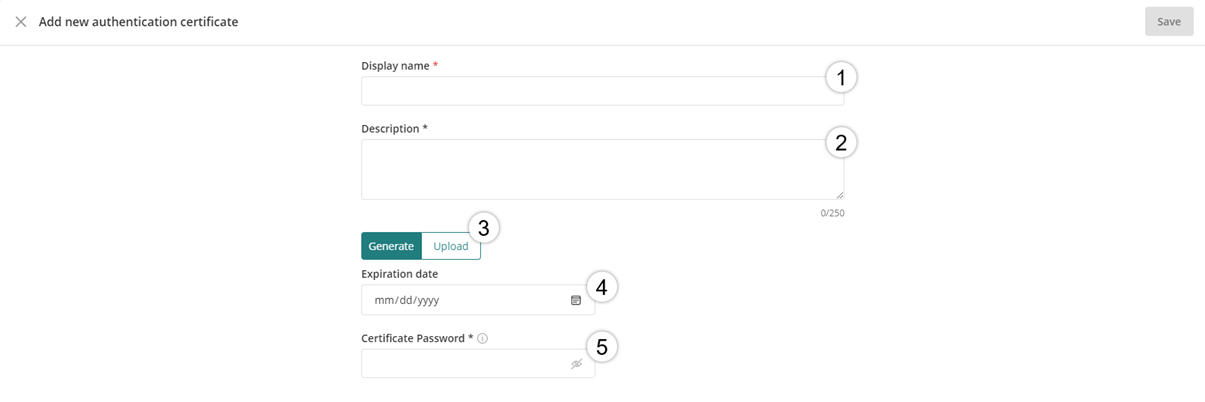
5.After all the required fields have been entered, click Save in the top right corner.

After the certificate is created a message will appear in the right bottom corner indicating it has successfully been saved.
To manage the generated security certificate in the Customer Portal refer to the Managing Authentication Certificates documentation.
2. Configure your IdP in Bizagi
After you configure the application in Entra ID, now you must access the Bizagi Studio or the Management Console and register the Identity Provider. Follow the steps in Configure a SAML 2.0 IdP in Bizagi.
3. Download the Bizagi metadata file
After you configure the identity provider in Bizagi, you must generate the metadata file. Refer to Download the metadata file.
4. Configure Bizagi as Service Provider in PingFederate
4.1. Login with admin rights to your PingFederate server.
4.2. Access the Idp Configuration menu and locate the SP Connections section.
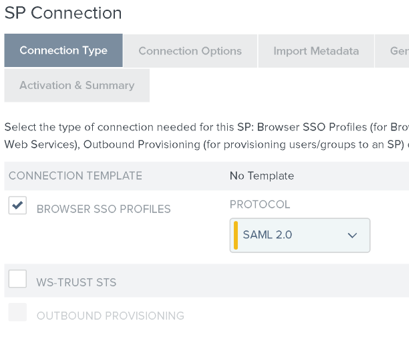
4.3. Click Create New for the Connection type, making sure that SAML 2.0 is selected as the Protocol:
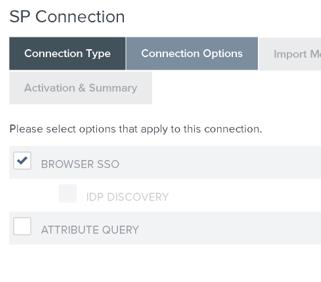
4.4. Check the Browser SSO checkbox on the Connection Options tab:
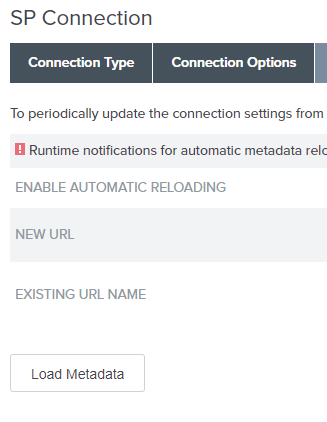
4.5. Use the Load metadata option on the Import metadata tab.
Browse for Bizagi's metadata.xml file for further configuration.
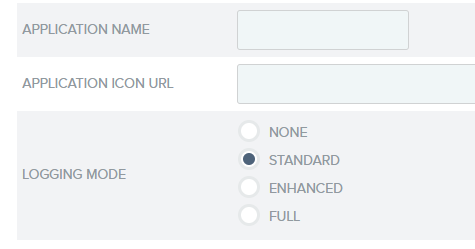
4.6. Confirm that Logging mode is set to Standard, on the General info tab.
Click Next when done.
4.8. Configure the Web browser and HTTP profile for message exchange.
First click Configure Browser SSO.
4.9. Click the SP-Initiated SSO and the SP-Initiated SLO checkboxes on the SAML Profiles tab.

Click Next when done.
4.10. On Assertion Lifetime tab, set the value for the minutes corresponding to the validity of issued assertions:
•Minutes before
•Minutes after
You may accept or modify defaults according to your policies.

Click Next when done.
4.11. Click Configure Assertion Creation on the Assertion Creation tab define which information the response assertions include.
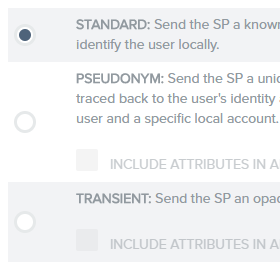
4.12. Select Standard mapping on the Identity Mapping tab:
4.13. Define the attribute taken as the base for the contract, at the Attribute Contract tab.
Enter in the SAML_SUBJECT either:
•domain\username
•username@domain
If the SAML_SUBJECT has a different format, you can set it to use the email while extending the contract to include the Email attribute:
urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
4.14. Click Map New Adapter Instance on the Authentication Source Mapping tab.
4.15. On the Adapter Instance tab, establish a new adapter for IdP Adapter Mapping by clicking on Manage Adapter Instances:
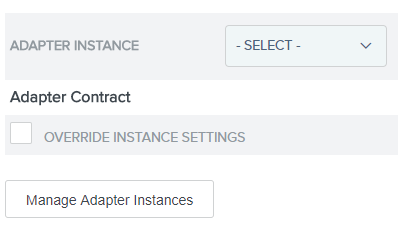
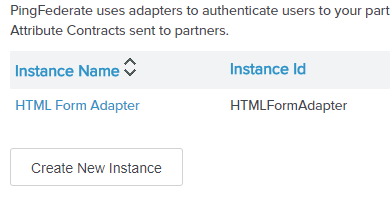
You can create a new one or select an existing one.
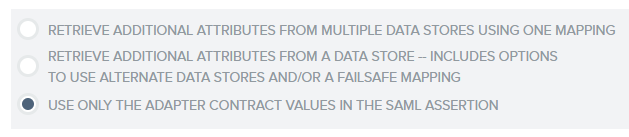
4.16. On the Assertion Mapping tab, select Use only the Adapter Contract values in the SAML assertion:
Click Next when done.
4.17. Select Adapter in the first drop-down list (Source) and Mail for the second one (Value), the SAML_SUBJECT fields on the Attribute Contract Fulfillment tab.
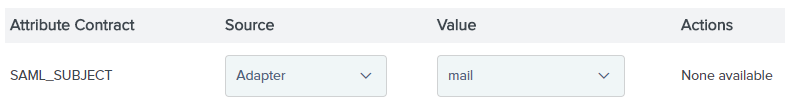
If the contract was extended in step #2.13 with the Email attribute, you need to select the same options from the drop-down lists (first Adapter, then mail) for the Email field that appears.
4.18. Skip the configuration presented on the Issuance Criteria tab.
Simply click Next.
4.19. Click Configure Protocol Settings in the Browser SSO section and review Protocol Settings.
The following configuration should be automatically filled out based on Bizagi's metadata file.
When reviewing this section overall or if you want to make manual changes, consider:
•On the Allowable SAML Bindings tab, only POST and REDIRECT values should be selected.
•On the Signature Policy tab, we recommend that you enforce that assertions are always signed and that signatures are required for Authn requests.
•On the Encryption Policy tab, make sure The Entire Assertion option is selected for encryption (instead of the Allow Encryption in SLO Messages from the SP option, which is not supported).
4.20. Click Configure Credentials on the Credentials tab and locate the Credentials section, to define security measures for messages between PingFederate and Bizagi.
4.21. Browse in the Digital Signature Settings tab for the certificate to sign assertions that are sent to Bizagi.
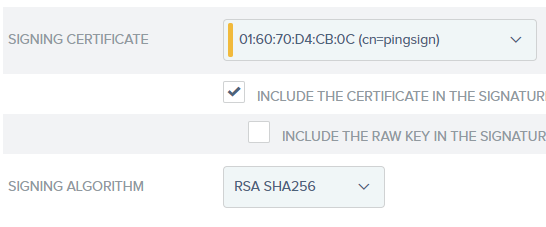
Select either SHA1 or SHA256 for the algorithm. This setting should match the algorithm defined in Bizagi parameters.
4.22. Define how the certificate will be validated by PingFederate whenever Bizagi signs messages.
For this, go to Manage Signature Verification Settings.
4.23. Select UNANCHORED in the Trust Model tab (to support self-signed certificates).
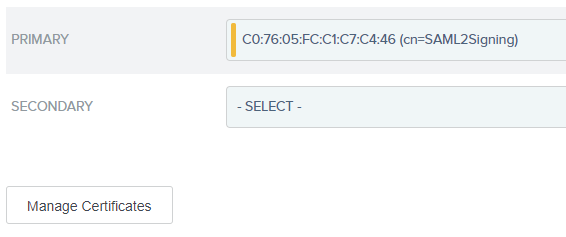
4.24. In the Signature Verfication Certificate tab, select the public key employed by Bizagi for signing purposes.
If this key is not selectable in the drop-down list, use the Manage Certificates button to first import it.
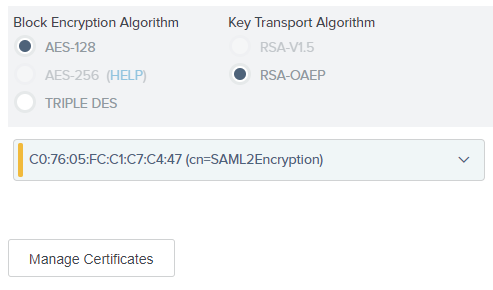
4.25. If you have enabled in Bizagi, that assertions will be encrypted, you need to select the certificate and algorithm used for this purpose (and follow this step and # 2.26).
For this, move to the Select XML Encryption Certificate tab and browse for the certificate.
Select AES-128 as the Block Encryption Algorithm and RSA-OAEP as the Key Transport Algorithm.
If your certificate is not listed in the drop-down list, you can import it using the Manage Certificates button.
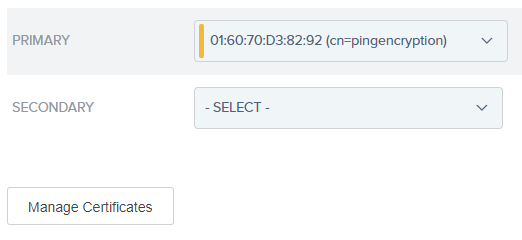
4.26. Move tto the Select Decryption Keys tab and browse for the certificate Bizagi uses to encrypt messages sent to PingFederate.
If your certificate is not listed in the drop-down list, you can import it using the Manage Certificates button.
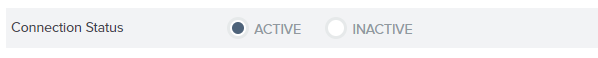
4.26. Finally, make sure that the Connection status is set as Active on the Summary page.
Make sure your changes are saved and exit when done.
Additional step
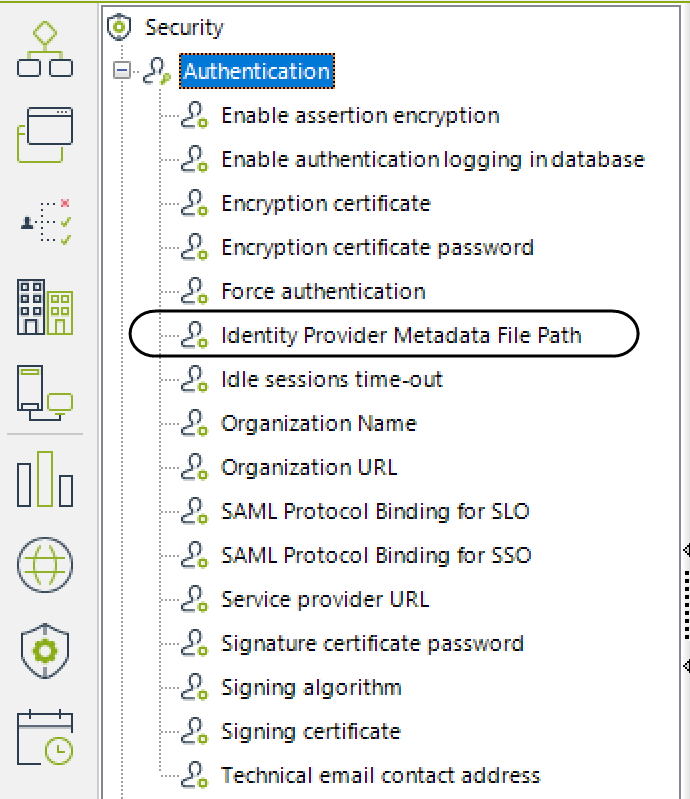
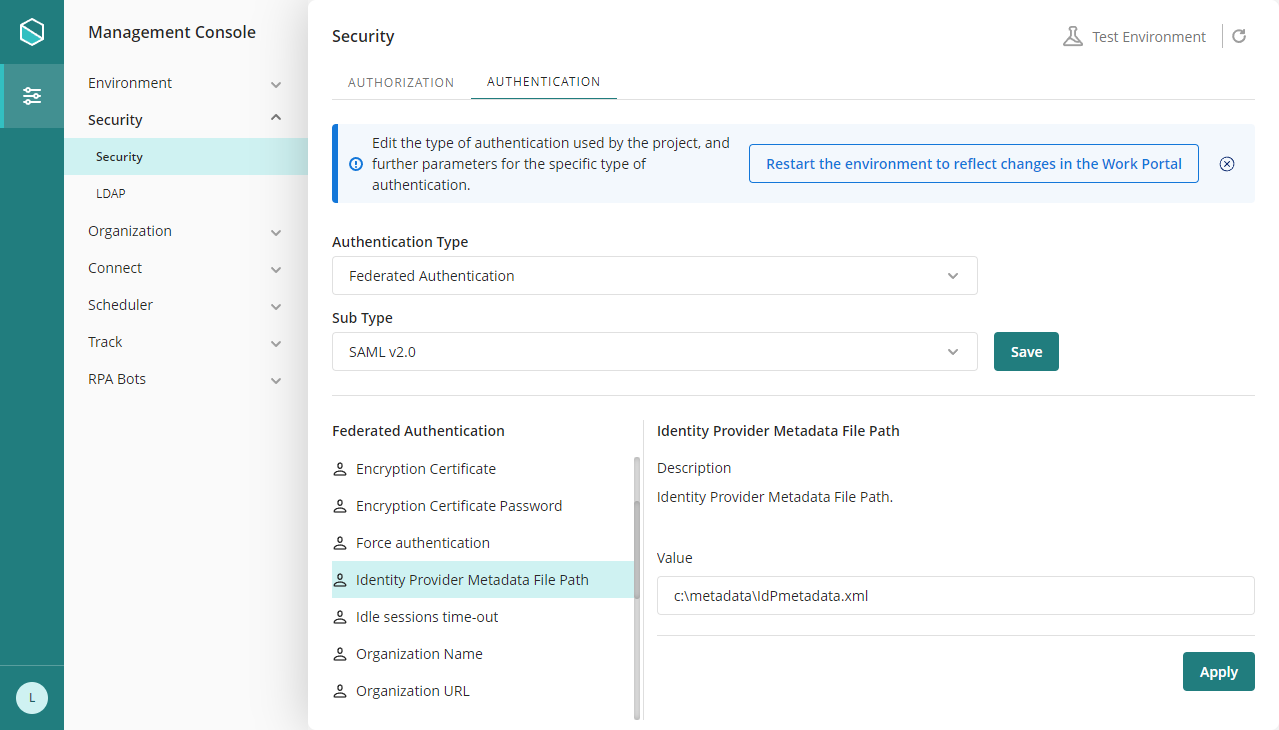
When you configured settings in Bizagi, you left the Identity Provider Metadata File Path blank.
To complete that setting, you need to obtain PingFederate metadata file.
Once you have this file's URL, go back to Bizagi Studio or the Management Console and set it in this key:
|
In the management console, before modifying the authentication configurations, it is necessary to set the environment status as Maintenance from the Maintenance window. After doing the desired modifications, remember to restart the environment to reflect the changes. |
Save your changes
You have configured your PingFederate to rely on SAML 2.0 for an integrated authentication with Bizagi!
Last Updated 12/10/2025 12:24:15 PM