Overview
After configuring SCIM in the Work Portal, the next step is to configure Entra ID.
|
Bear in mind that for the configurations you must have a Client Secret, obtained from Bizagi Work Portal. |
Prerequisites
•Your Entra ID tenant.
•A user with permission to configure Entra ID like Application administrator, Cloud Application administrator, Application Owner or Global Administrator.
•Security Groups of applicable users by environment.
Provisioning
1. Open the Azure Portal as the administrator, and access your Azure Active Directory.
2. Add a New Application.
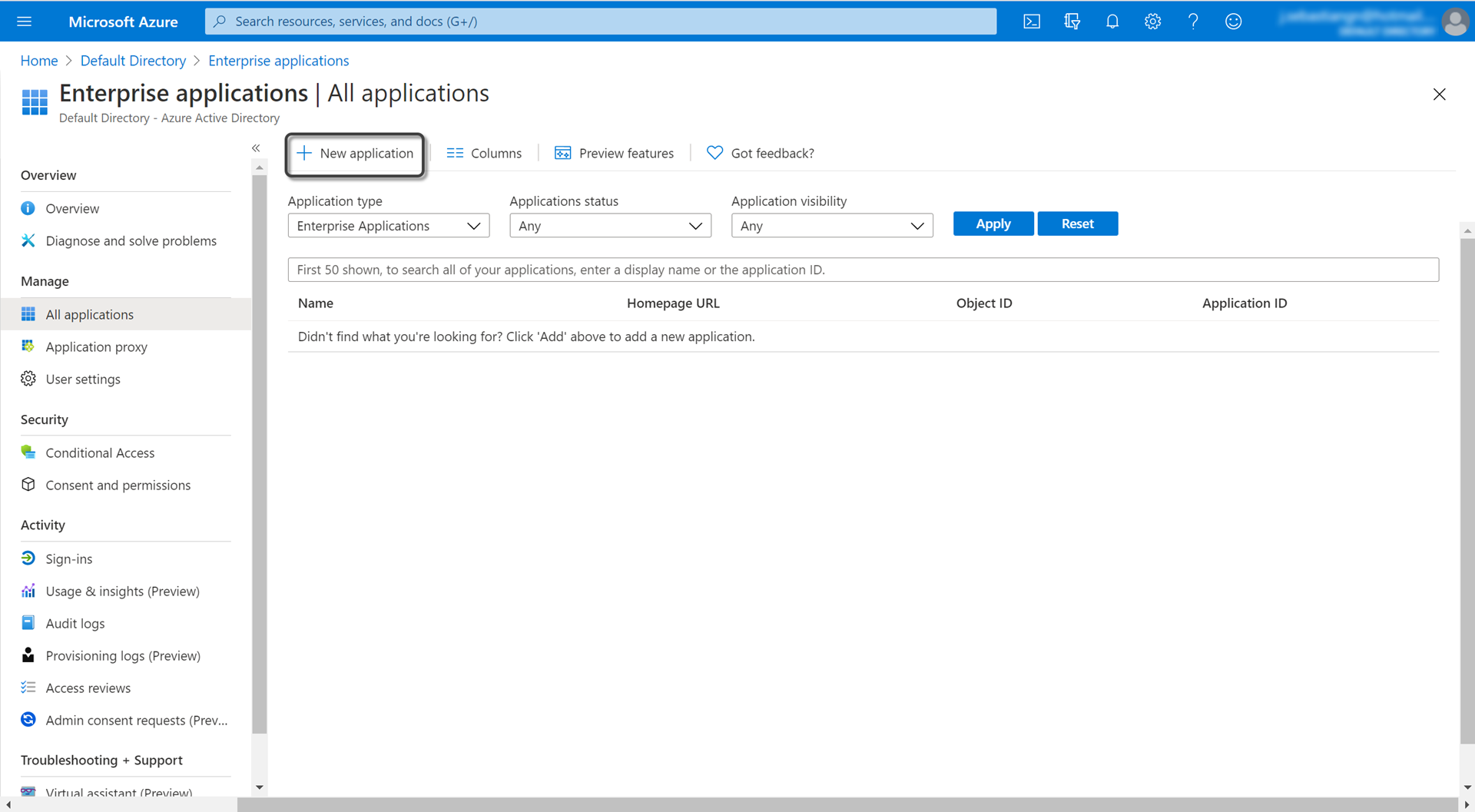
Browse Bizagi and select Bizagi Studio for Process Automation.
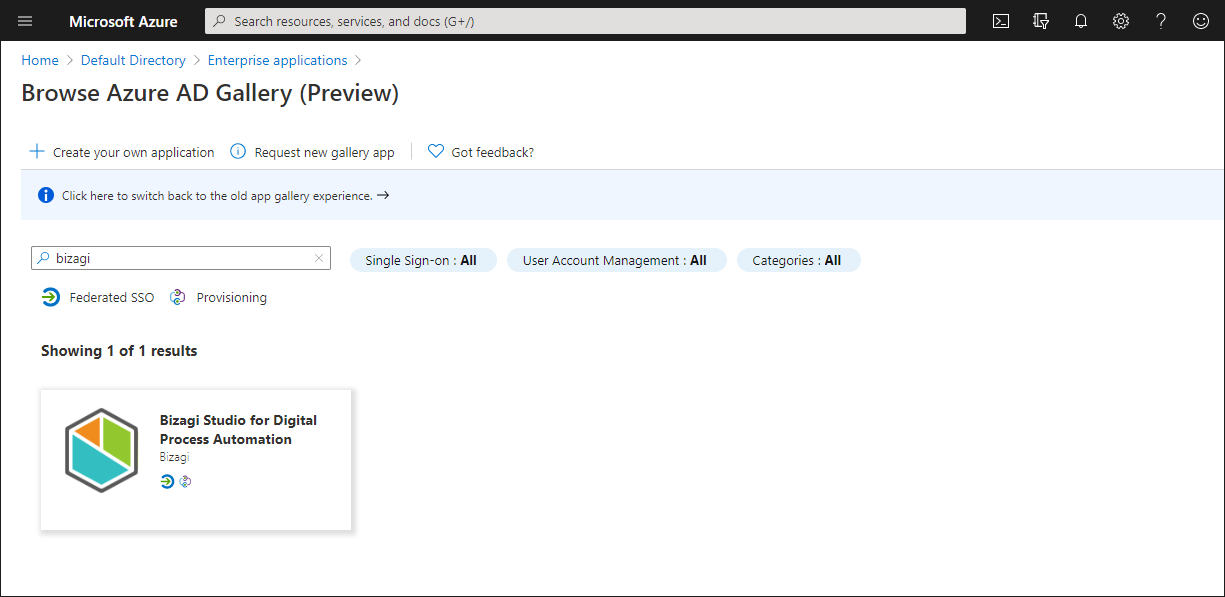
3. Give your application a name and click Create.
|
When you name your application, use word that relate to the environment in which the configuration will be applied and include the name of the service that you are going to use, for example "Work Portal" or "Customer Portal". |
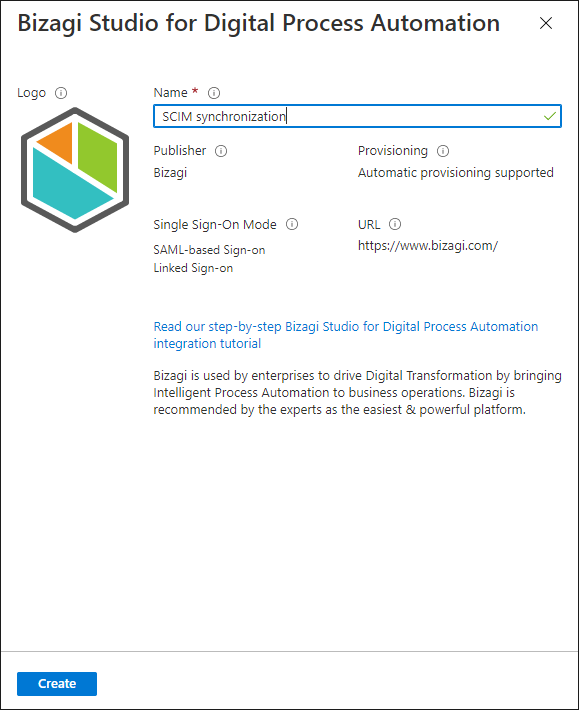
4. Access the Manage menu and click Provisioning.
5. Select Automatic Provisioning Mode.
6. Go to Users and Groups and assign the Security Group you defined as a prerequisite.
7. Register the following Admin Credentials.
•Tenant URL: Enter the Bizagi SCIM endpoint with this structure:
[Your_Bizagi_Project]/scim/v2/
Example: https://my-company.bizagi.com/scim/v2/
•Secret token: The Client Secret, as the Bearer Token, generated in OAuth 2.0 Applications inside Bizagi's Work Portal.
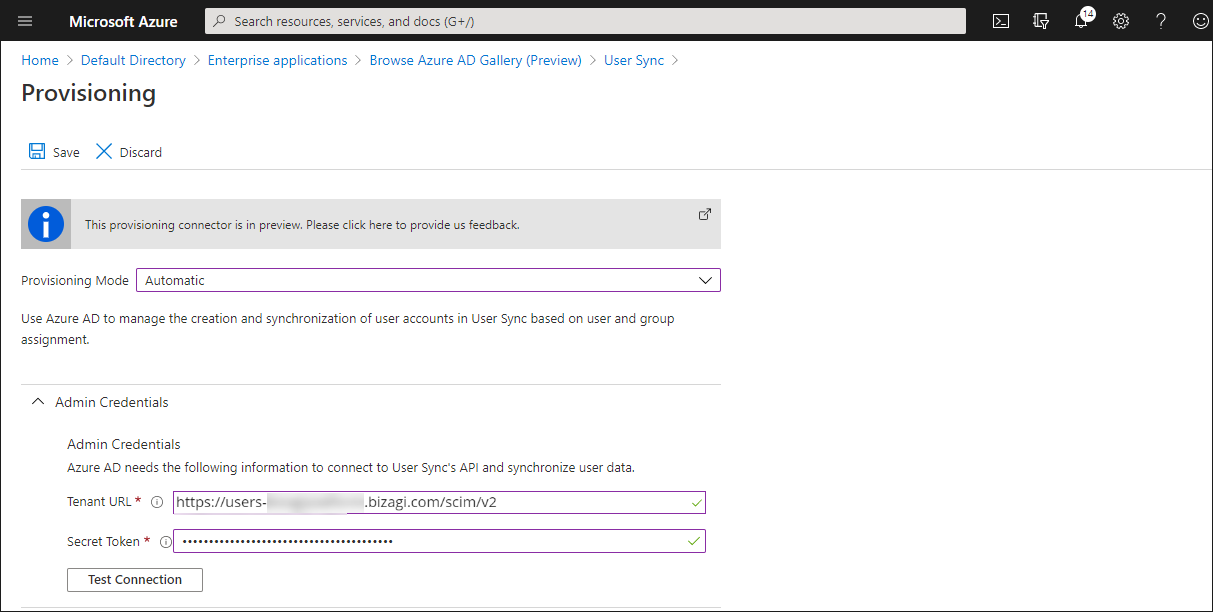
|
The Tennant URL structure is the following: http://users-subscriptionName. bizagi.com/scim/v2 |
8. Click Test Connection and wait for a confirmation message.
9. Register the Notification Email a person or group who will receive error notifications. Make sure the check-box Send an email notification when a failure occurs is selected. Finally, click Save.
Attribute Mapping
You need to configure the mapping of user attributes between Entra ID and the WFUser table. To do that, click the Edit attribute mappings option in the Provisioning module:

Click the Provisioning Azure Active Directory Users.
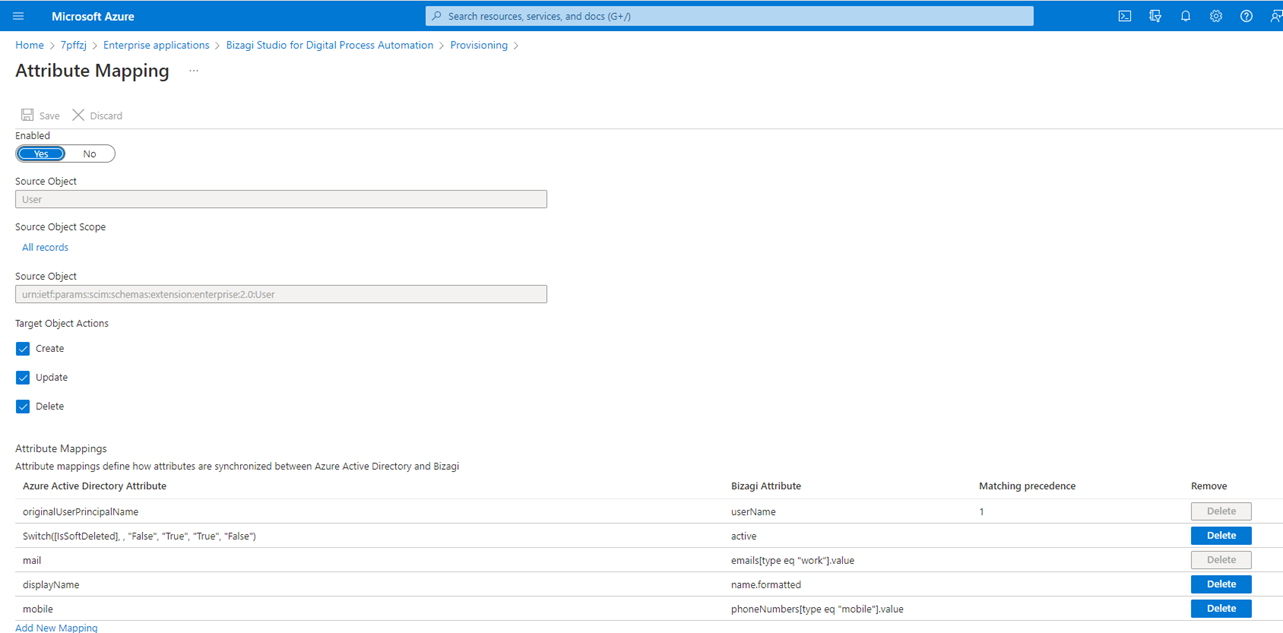
Then delete all the default attributes, and leave the following attributes:
Attribute name in Entra ID |
Attribute name in Bizagi |
Observations |
|---|---|---|
originalUserPrincipalName |
userName |
User domain cannot exceed 25 characters; otherwise, the user is not synchronized. |
Switch([IsSoftDeleted], , "False", "True", "True", "False") |
active |
A non active user is considered as a non existent user. Therefore is not synchronized. |
emails[type eq "work"].value |
This is a mandatory field. |
|
displayName |
name.formatted |
This is a mandatory field. |
mobile |
phoneNumbers[type eq "mobile"].value |
|
The configuration looks as follows:
You can also set the email as the Unique Identifier (UserName in Bizagi) when synchronizing users:

|
Using the user.mail as the Unique Identifier can be useful when you use the SSO configuration using the Bizagi Enterprise Application. See Using Bizagi Enterprise Application in Azure. |
Custom user properties
In Bizagi you can create customized user properties. Refer to How to create user properties. To learn how to map these customized user properties when synchronizing users from Entra ID, see Custom user properties mapping.
Synchronization Scope
Select the synchronization Scope, you can either choose the all users of the directory or users included within the Enterprise application's Users and groups.
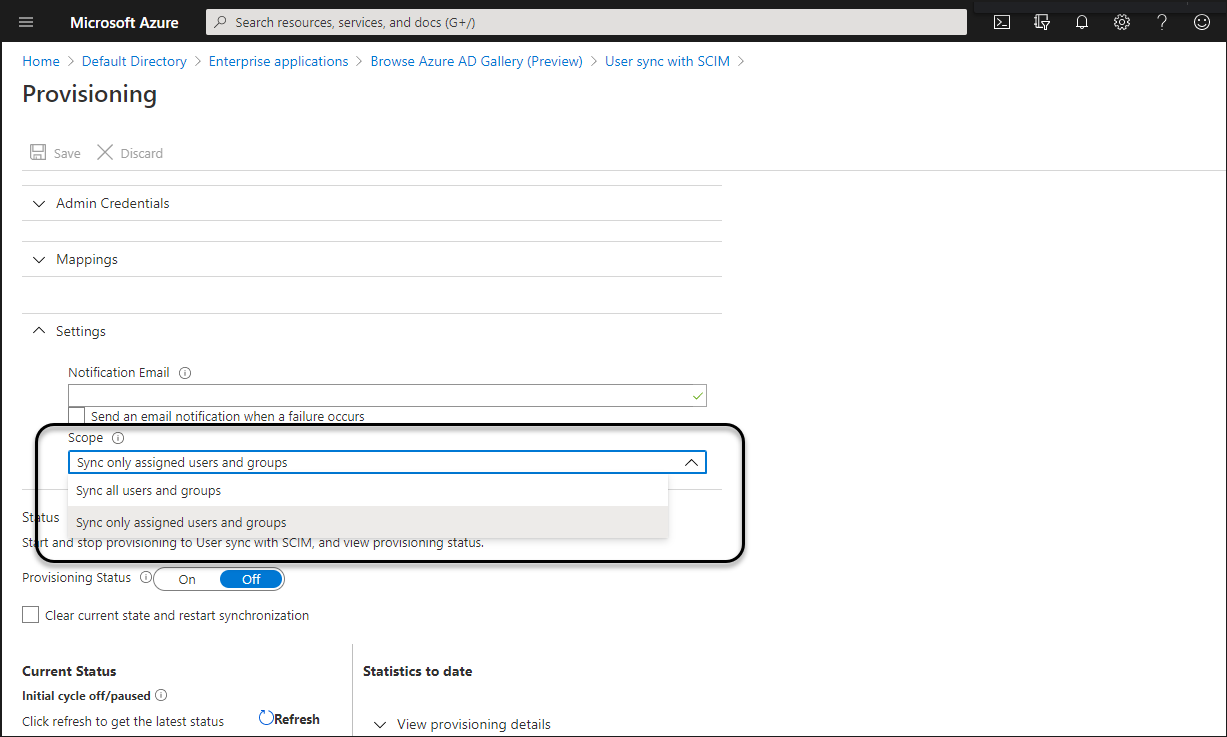
Enabling the synchronization
To enable the synchronization of users to Bizagi, you must open the Provisioning options, switch on the Provisioning Status, and then click Save.

After saving, Entra ID starts the initial user synchronization based on your scope. This lasts longer than subsequent cycles because is the first user synchronization.
Last Updated 9/11/2024 10:26:27 AM