Overview
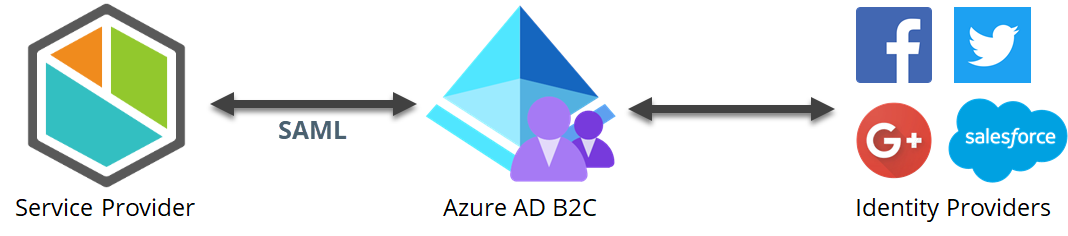
Entra ID B2C is an Identity Access Management system that enables users to use social, enterprise or personal accounts to get SSO access to the application where is configured.
This article provides a step-by-step guide about the configuration needed, both in Entra ID and in Bizagi, to integrate your authentication in Bizagi through Entra ID B2C. Note that these steps are done only once, typically by an admin user of your Customer Portal having access to your Entra ID B2C.

Once you have carried out these steps users sign in to any cloud-based service directly via your Entra ID, as described at Signing in the Bizagi Cloud Portals and Applications.
Before You Start
To configure Entra ID B2C supporting SAML 2.0, you need:
•Have a resource with an Active Directory B2C.
•Create a B2C Tenant inside the Entra ID B2C. To know how to create a B2C Tenant, click here.
Associate the SAML 2.0 protocol with the B2C
Configure the necessary policies to support SAML 2.0
To do so, go to your tenant configuration and go into the Identity Experience Framework.
|
Bear in mind that you need to be in the subscription and in the active directory where the B2C tenant was created. |
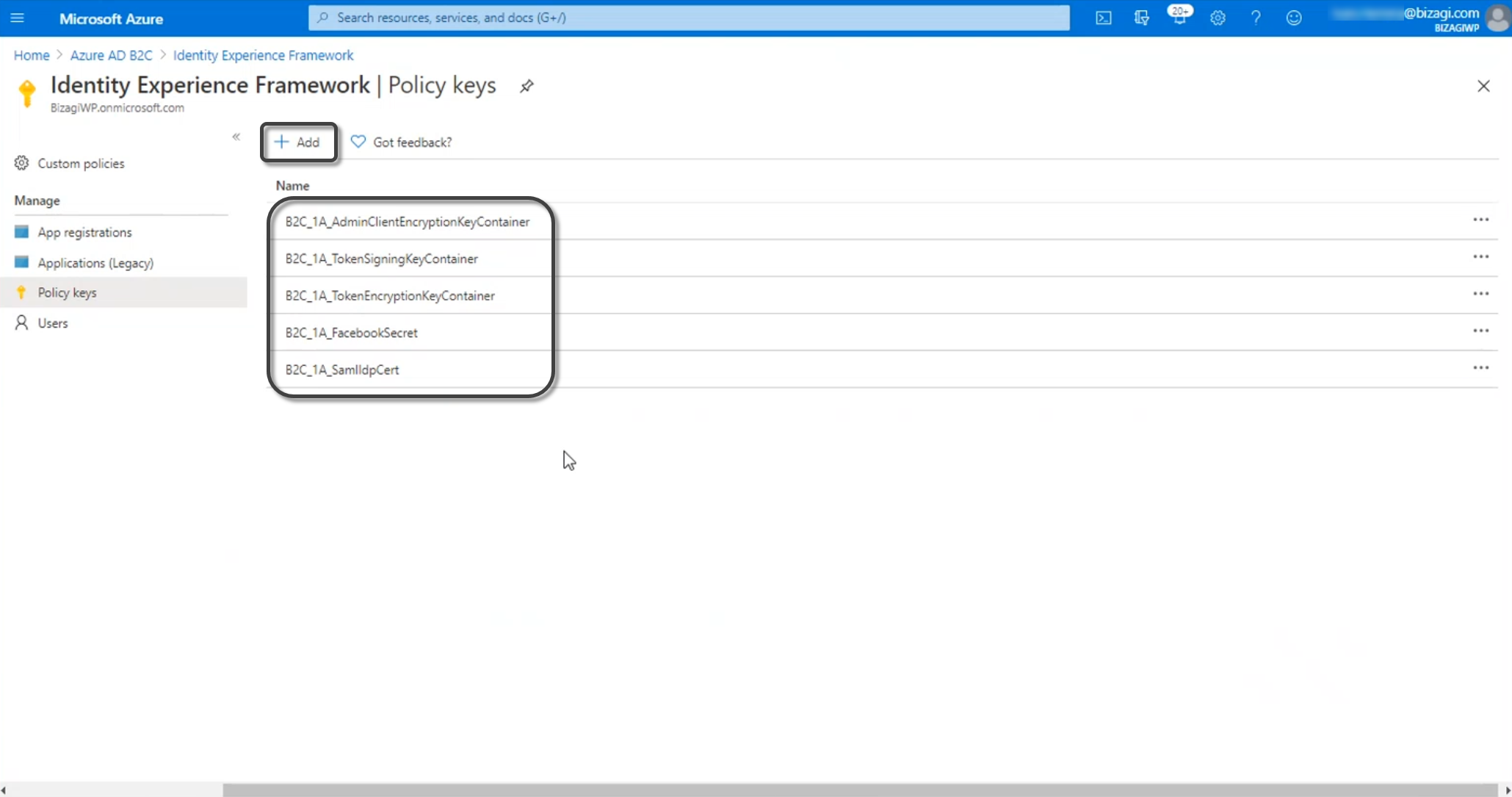
Create the Policy Keys needed to establish trust with the services that you are going to integrate with. For this, click Policy Keys and then click Add.
Register a SAML application in Entra ID B2C. For more information about registering a SAML application in your Entra ID B2C, click here.
To know more about custom policy keys, click here.
Now follow these configuration steps.
1. Generate certificates to sign assertions (mandatory)
The following explains how to generate the security certificate from the Customer Portal:
|
You will need to be in charge of managing your installed certificates (keep track of its expiration date and other relevant maintenance aspects such as changes in your Identity Provider's endpoints). |
Create Authentication Certificates
You can generate security certificates for the Authentication Protocols within the Customer Portal. This feature allows you to create and configure a new certificate or upload an existing one in the Customer Portal. To setup the Single Sing On and access the Customer Portal, sign on to your account role as a Company Administrator. This user role can this user can create users in the company user's pool, and manage users in all the company subscriptions. For additional information about Managing Customer Portal and roles refer to:
To create a security certificate inside the Customer Portal follow these steps:
1.Select the Settings icon located in the left panel menu.
![]()
2.A panel expands from the left with all the security related topics. Select the Authentication certificates option.

3.Inside this section, there is a list of certificates with details like Name, Description, Expiration date, Owner and Creation date and its creation source. In the top right corner, select the Add certificate button.

4.The Add new authentication certificate window opens for you to create the new security certificate and you must fill out the five different required fields:
a.Display Name.
b.Description.
c.Either select the Generate (to create a new certificate) or Upload (to upload a existing certificate) option for the toggle button.
d.Expiration date.
e.Certificate password.
When you select the Generate option, set the Expiration date and assign a Certificate password. If you select the Upload option, you are required to upload digital certificates files in a PFX or a P12 format and then, select the type of algorithm to implement between SHA256 and SHA1. For last, enter the password from the certificate.
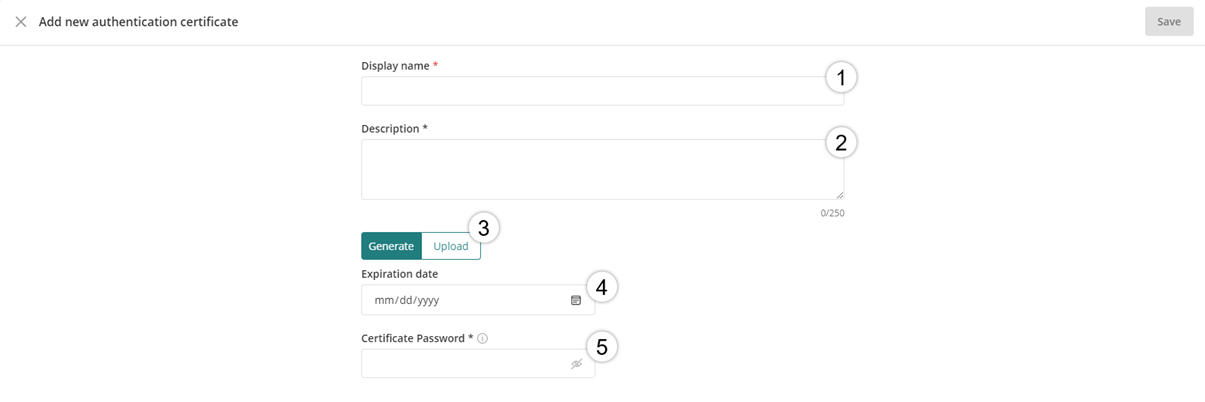
5.After all the required fields have been entered, click Save in the top right corner.

After the certificate is created a message will appear in the right bottom corner indicating it has successfully been saved.
To manage the generated security certificate in the Customer Portal refer to the Managing Authentication Certificates documentation.
2. Configure your IdP in Bizagi
After you configure the application in Entra ID, now you must access the Bizagi Studio or the Management Console and register the Identity Provider. Follow the steps in Configure a SAML 2.0 IdP in Bizagi.
3. Download the Bizagi metadata file
After you configure the identity provider in Bizagi, you must generate the metadata file. Refer to Download the metadata file.
4.1 Log in to your Azure services with a user account with admin rights.
Access your Azure subscription with the Entra ID service.
You will need to sign into Azure's portal at https://portal.azure.com.

Make sure that you need to be in the subscription and in the active directory where the B2C tenant was created.
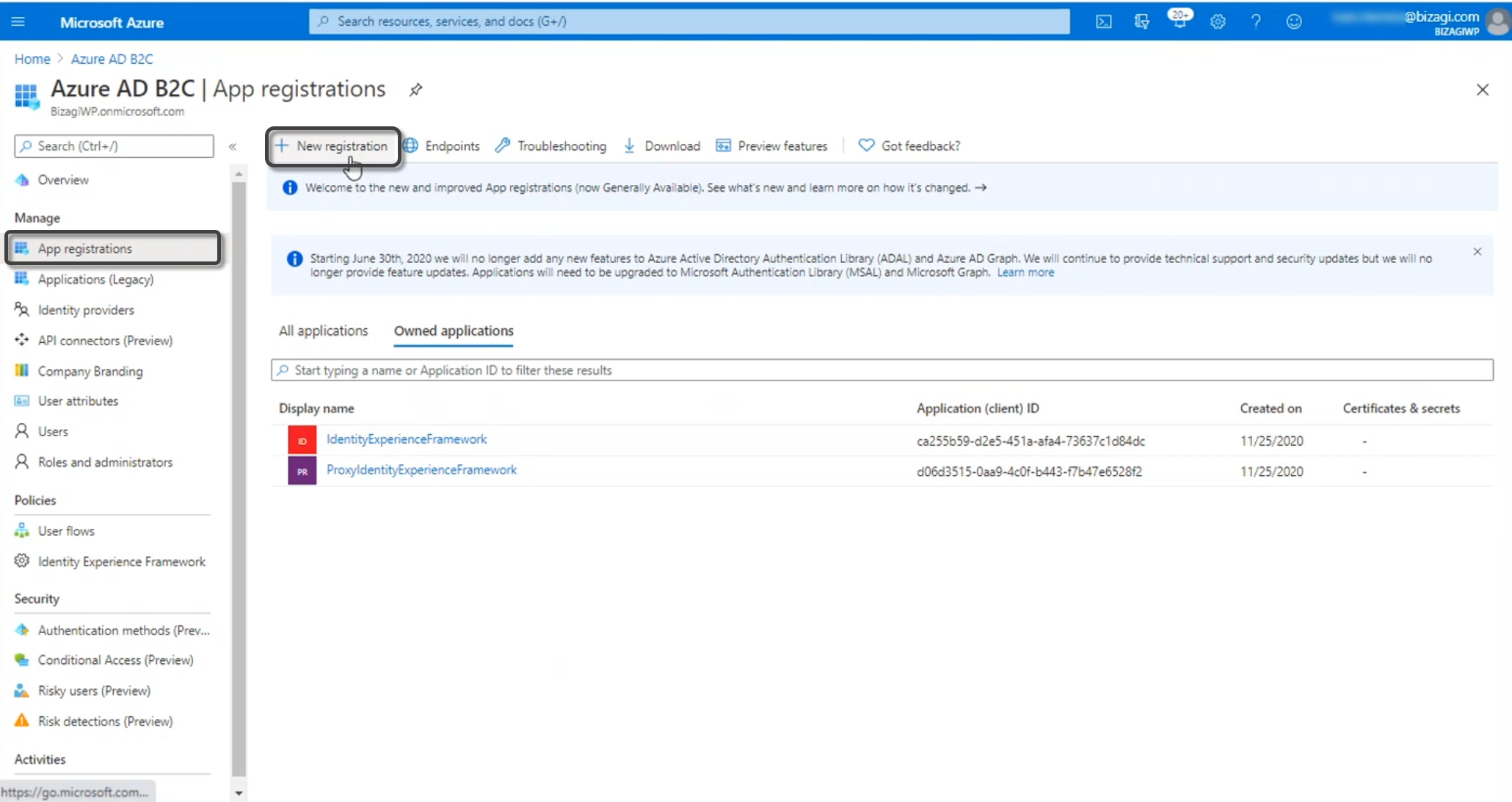
4.2 Register the Application
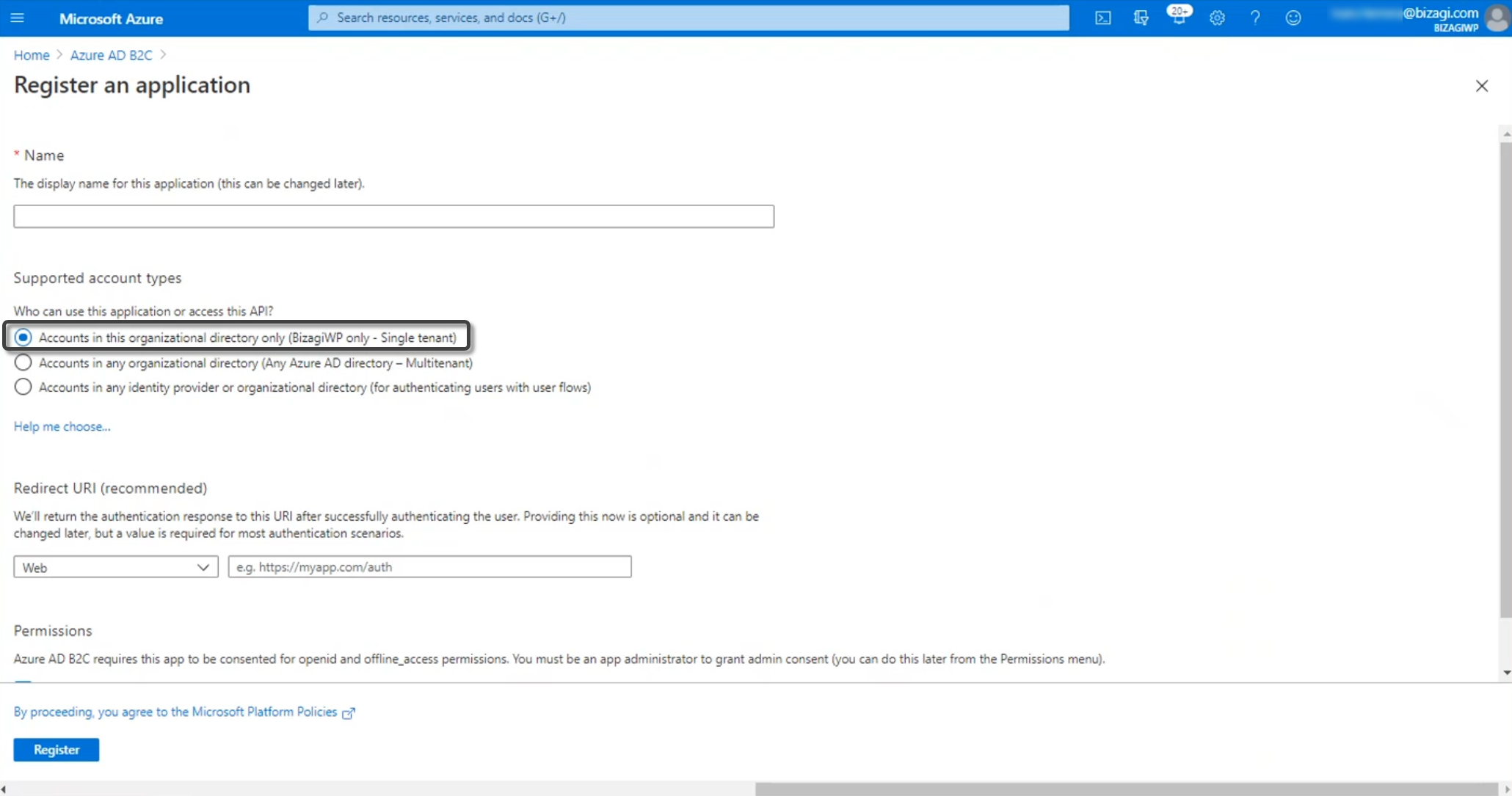
Open the Entra ID, and select the App registrations menu. Click New registration:
Give a name to your application. Then, select the supported account types. Make sure that you select the tenant associated to the B2C. Finally, type your project's URL.
4.3 Change the application manifest
Once your application is registered, you will be able to see it in the App registrations menu. Go to the application.
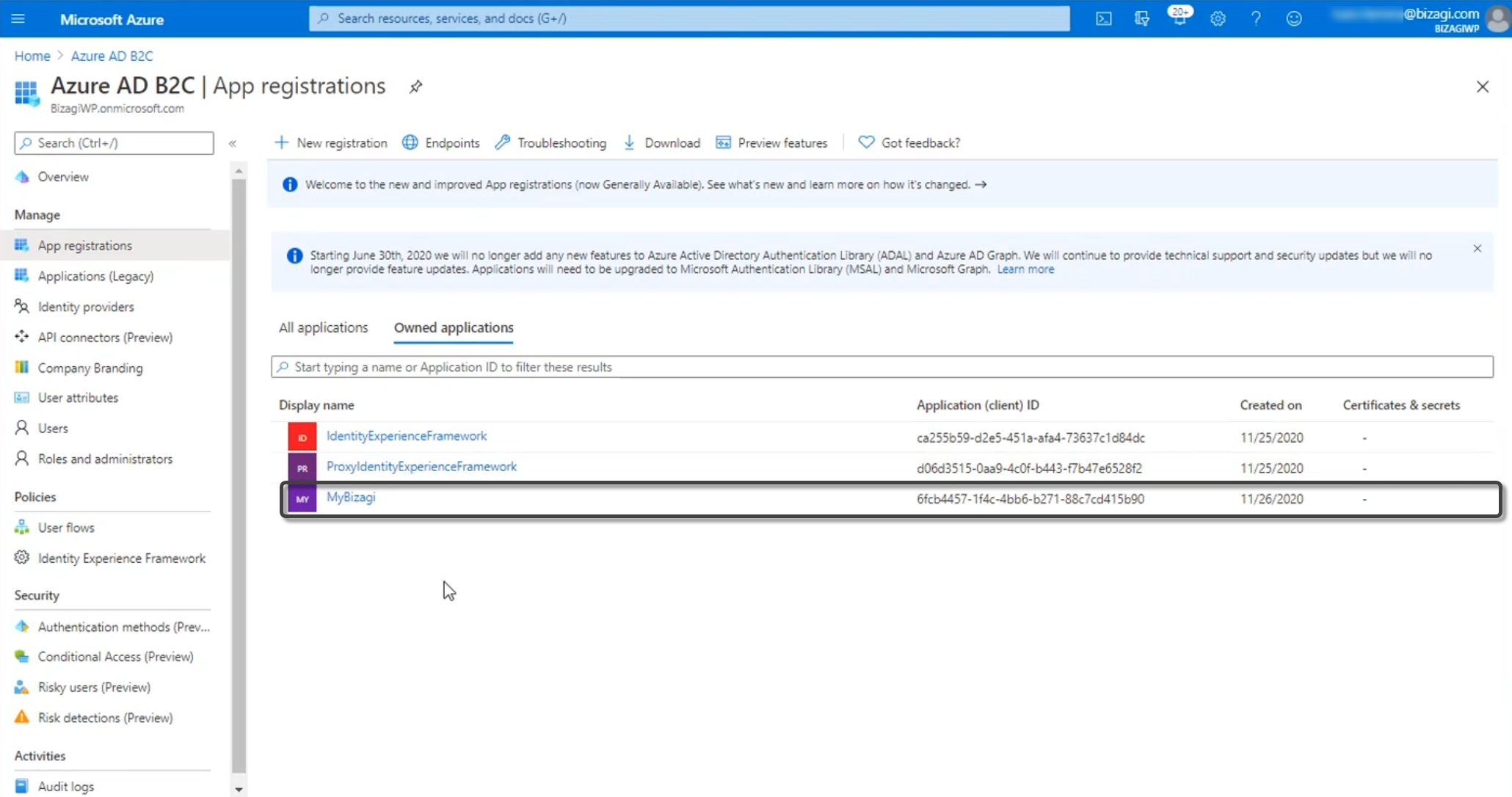
In the manifest, change the following parameters with the values below:
•identifiersURIs: https://[environment]-[project]-[company].bizagi.com
•logoutURl: https://[environment]-[project]-[company].bizagi.com/saml2/logout
•replyURL withType
ourl: https://[environment]-[project]-[company].bizagi.com/saml2/assertionConsumer
•samlMetadataURL; https://[environment]-[project]-[company].bizagi.com/saml2/metadata?mode=preview
•signInURL: https://[environment]-[project]-[company].bizagi.com
Additional Keys
You must add the following key accessTokenAcceptedVersion and must have the value 2:
"accessTokenAcceptedVersion" : 2
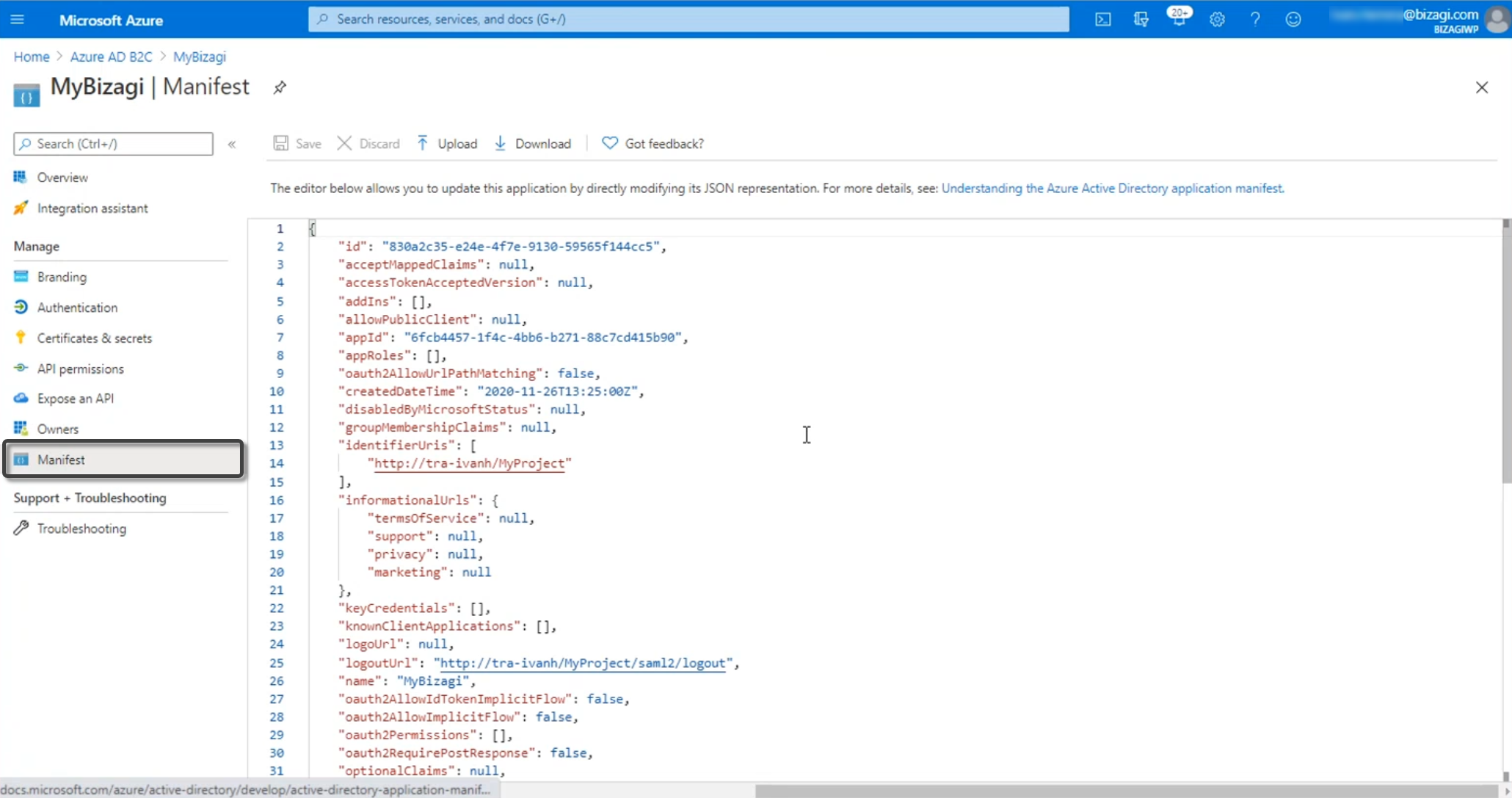
Go to the Identity Experience Framework and open the TrustFrameWorkBase file.
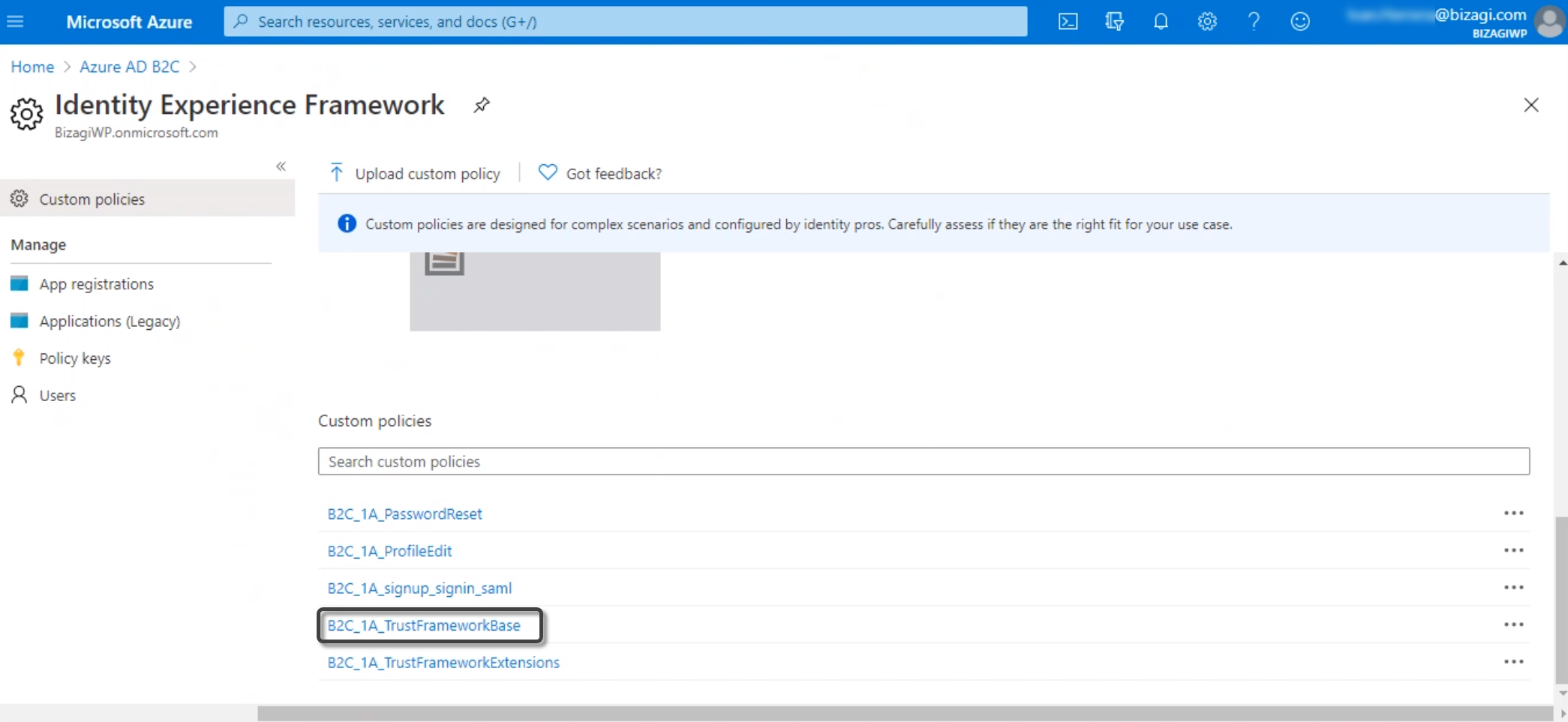
Look for the TechnicalProfile node associated to the SAML protocol. Inside, copy the IssuerUri, which is the metadata URL associated to the SAML assertions generator.
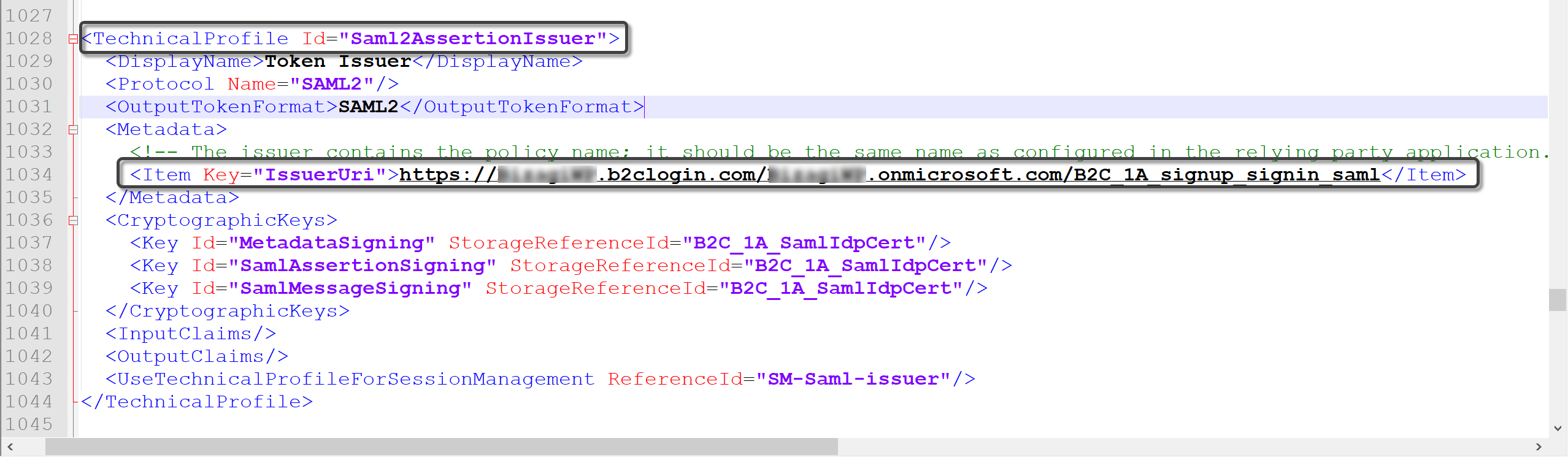
Finally, add the following suffix to the URL copied: Samlp/metadata
|
The metadata URL must have the following format:
https://<B2Ctenant>.b2clogin.com/<B2Ctenant>.onmicrosoft.com/B2C_1A_signup_signin_saml/Samlp/metadata
where <B2Ctenant> is the name of the B2C tenant created in the Entra ID B2C. |
Once you have this file's URL, go back to Bizagi Studio or the Management Console and set it in this key:
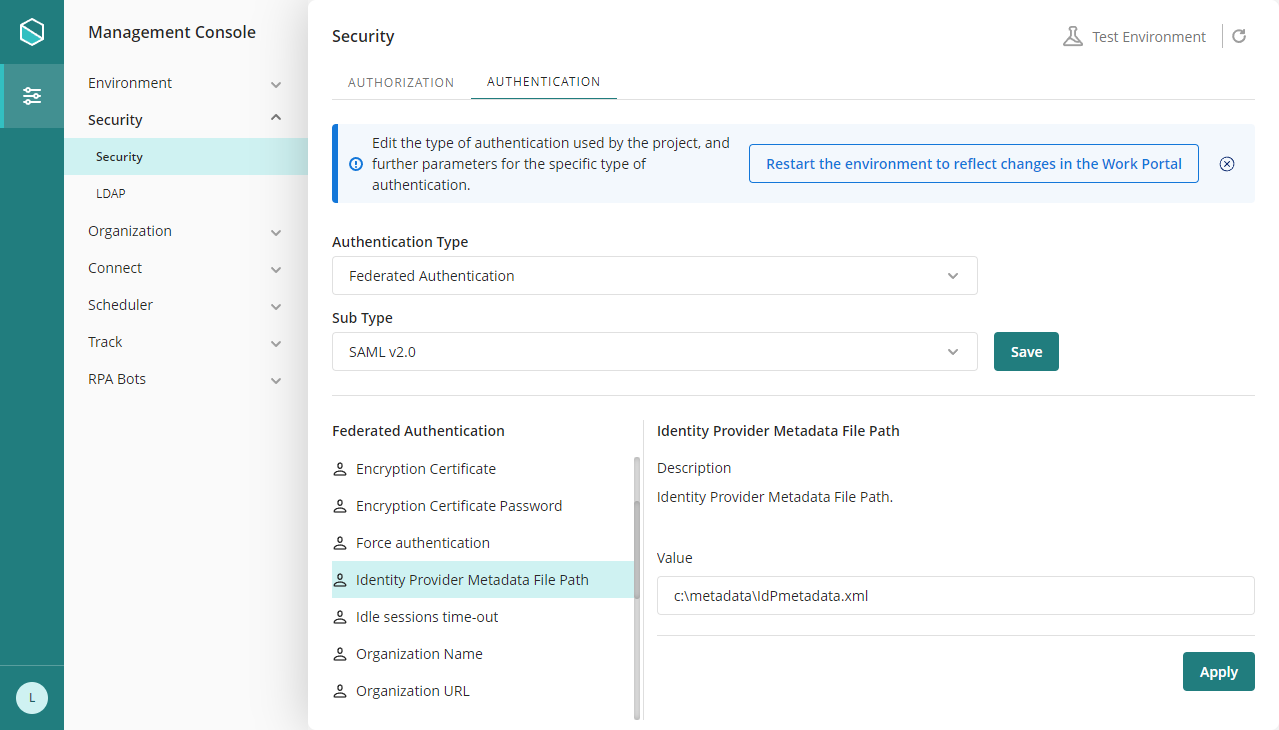
|
In the management console, before modifying the authentication configurations, it is necessary to set the environment status as Maintenance from the Maintenance window. After doing the desired modifications, remember to restart the environment to reflect the changes. |
Now when you run the Work Portal, Bizagi displays the IdP's log-in page and users can be authenticated with your IdP.
|
Remember to do this configuration in all your environments, or to deploy security configurations in your target environments, for example, test or production environments. |
Last Updated 12/10/2025 12:21:53 PM