Overview
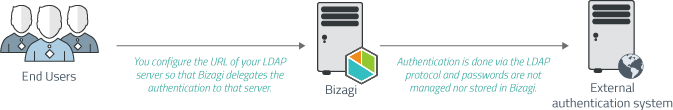
When using LDAP Authentication in Bizagi, credentials entered in the login page (username, password and domain) are sent to an LDAP Server for verification.
Once the server verifies and permits the access, login is successful as long as this user is already created in Bizagi.
In this authentication, passwords are never stored in Bizagi.
|
If you plan on using an authentication method different than Bizagi and you are performing a deployment to an environment with no users on it (normally this would only be the case for a project's first deployment), follow these steps so that you can correctly configure your users and authentication without getting locked out of the Work Portal: 1.Perform the deployment with the authentication method set to Bizagi. This lets you access the Work Portal as the Admon user without providing any credentials. 2.Once in the Work Portal you can manually enter your users, or alternatively you can rely on the method of your choice to synchronize your users' information into the WFUser table (SOAP, Excel file, LDAP Synchronization, or performing a Data Synchronization procedure). 3.After having your users registered in the Work Portal, use the Management Console to set the authentication method to your preferred one.
If you plan on using LDAP authentication with periodic users synchronization, you may ignore the previous steps since you will only need to wait until the next synchronization happens for your users to be able to log into the Work Portal. |
Setting LDAP Authentication
To set LDAP as the authentication type, select LDAP from the drop-down list:
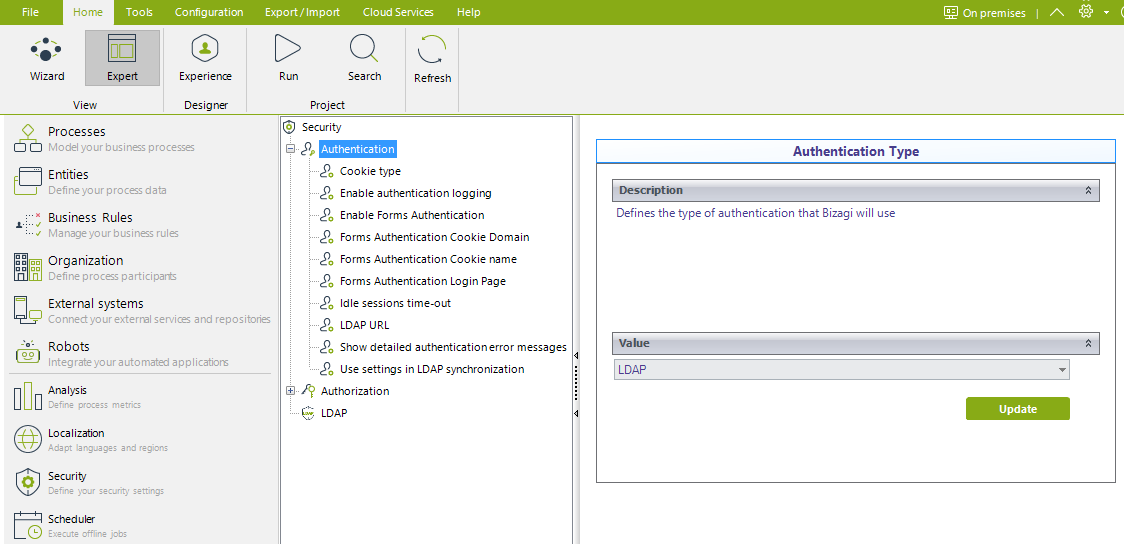
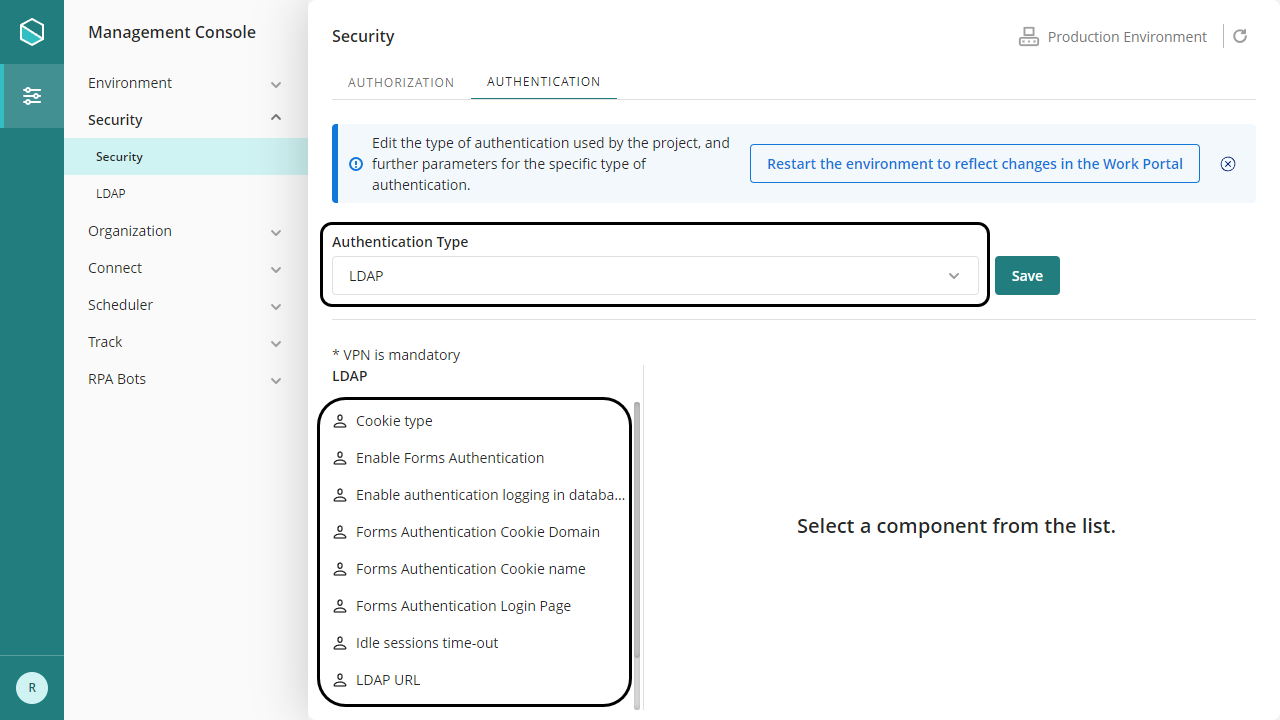
You can also set or change these parameters from the Management Console.
|
In the management console, before modifying the authentication configurations, it is necessary to set the environment status as Maintenance from the Maintenance window. After doing the desired modifications, remember to restart the environment to reflect the changes. |
Click on the Save/Update button.
The following options presented as inner items must be configured:
•Cookie type: Defines whether Bizagi uses Persistent o Session cookies. The idle session time-out defines the expiration time for cookies.
•Enable authentication logging: Establishes if an audit log is recorded with all authentication events. If enabled look for the table AUTHOLOG in the database.
•Enable Forms Authentication: enables the extension feature to Bizagi with the ASP.net Forms authentication protocol, based on using forms to authenticate users. For more information visit Forms Authentication.
•Forms Authentication Cookie Domain: type the domain of the Cookie in the available field.
•Forms Authentication Cookie name: type the name of the Cookie used.
•Forms Authentication Login page: set the URL of the login page that Bizagi redirects in case the session expires or the authentication fails (e.g. using the wrong password).
•Idle session time-out: Defines the time in minutes in which an idle session expires; in which case it would be required to authenticate again. This setting defines the expiration time for cookies. You should not set this time-out to more than 60 minutes.
•LDAP URL: Corresponds to the path to access the LDAP Server (using the LDAP URL format).
It is mandatory that you input LDAP://.. with the starting LDAP prefix in uppercase, capital letters.

•Show detailed authentication error messages: Defines if authentication errors are shown in a detailed way when they occur.
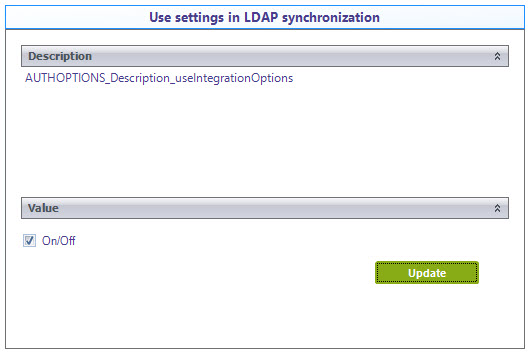
•Use settings in LDAP synchronization: Applies if you already have configured Bizagi to synchronize your Active Directory users into Bizagi.
If this is the scenario, turn this option on, to use the same LDAP URL and settings from the LDAP synchronization settings.
When this option is on, the value of the former option will be ignored.
|
Windows Active Directory is supported as for LDAP authentication. |
Importing Users
or any type of authentication, you will need to make sure that users are created at Bizagi Work portal.
Disregarding the selected Authentication type for your Work Portal login, you may choose to configure a schedule in Bizagi to import and synchronize users from your Identity provider into Bizagi.
For more information about this option, refer to Synchronizing users.
About Anonymous authentication
Bizagi, like any other modern web application, bases its architecture on thin clients that consume web services (REST) from the business logic layer.
Bizagi is fully committed with the security, and decides to take complete control of the way in which these services are secured. Through filters at the request level, and with validations in every single service, the authentication and authorization modules of the Product guarantee that the different operations can only be executed by authorized users.
The static resources (html, js, css, images) that make up the login page must be exposed publicly and without restriction, only in those environments and configurations where it is necessary to display it: in the mobile application and in the web application when it is exposed to the Internet.
Last Updated 12/10/2025 12:22:35 PM