Overview
Forms authentication is not a Bizagi authentication method per Se, but rather an extension feature for your Bizagi, LDAP or Custom authentication. Once you enable this extension, you can use Bizagi with the ASP.net Forms authentication protocol, based on using forms to authenticate users.
The main advantages of using Forms authentication in Bizagi is that you can use a specific shared cookie to authenticate for several different applications that share the same Forms authentication configuration. With this feature, when an external application generates an authentication cookie based on Forms Authentication, Bizagi can log in with it and doesn't needs to request credentials.
Enable Forms authentication
To enable Forms Authentication follow these steps:
1.In the expert view, go to the Security node.
2.Under the authentication node find the option Enable Forms Authentication.
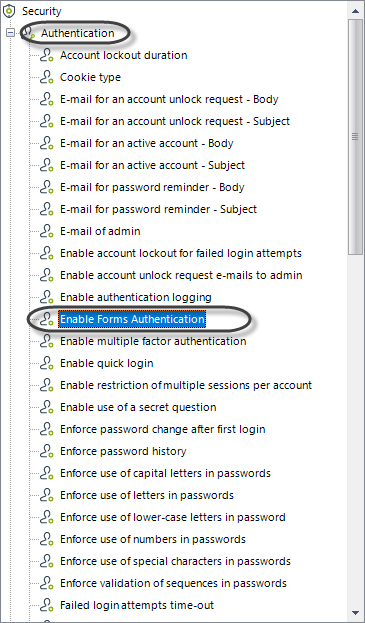
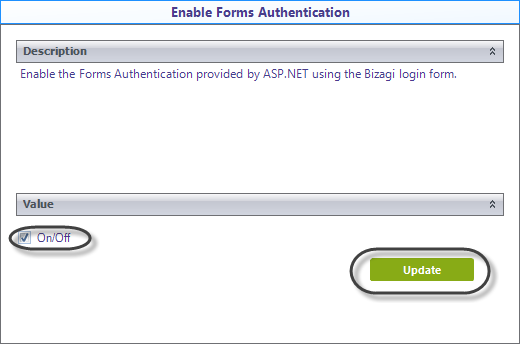
3.Select the On/Off check-box and click update
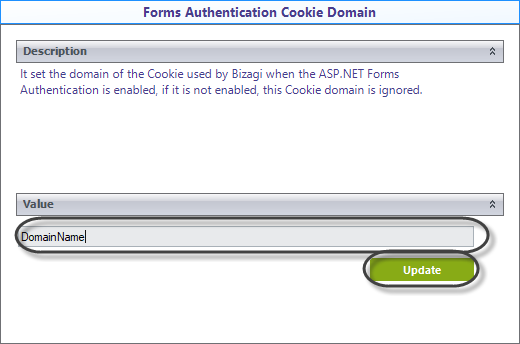
4.Next go to the Forms Authentication Cookie Domain option and configure your domain in the available field. Once you've typed your domain, click Update.
|
To use any external application with the same cookie, it must be in the same domain as the one configured in this field. |
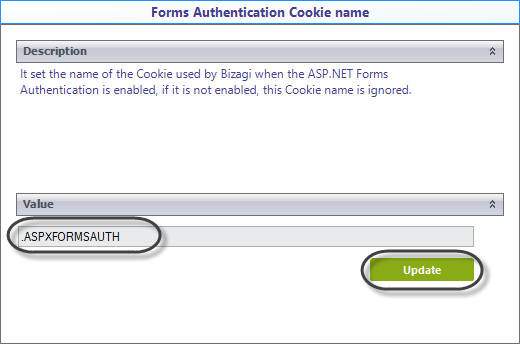
5.To set the cookie name, go to the Forms Authentication Cookie name option and type your cookie name in the available field.
6. You can set the URL of the login page that Bizagi redirects in case the session expires or the authentication fails (e.g. using the wrong password).
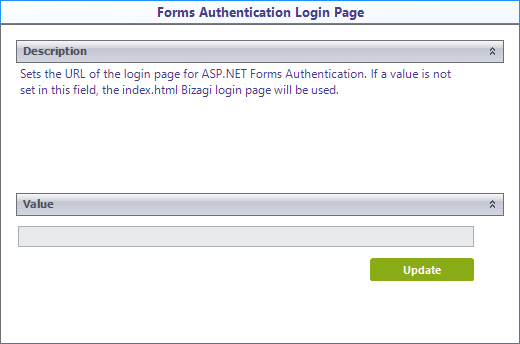
Hence it replaces the Bizagi login page, for example, values such as https://mycompany/formsauthentication/login.html can be placed. If you want to use the default Bizagi login page, you must leave this field blank or enter the index.html value.
Be careful not to place the complete Bizagi URL in this field, otherwise you can have an infinite loop when trying to enter to Bizagi.
|
When Mixed authentication is configured, the settings of the Mixed authentication overcome settings of each individual authentication methods. For example, if Mixed authentication is enabled using Bizagi and Windows, only the settings of form authentications are considered in the Mixed authentication node. |
Cookie considerations
To use the same cookie generated by other applications, keep in mind the following restrictions:
•Both the external application and Bizagi must have the same Machine Key configuration in the Web.config.
•To use any external application with the same cookie, they must share the same exact cookie name.
•The cookie must have in its authentication token as the first value. This authentication token must follow the following format: domain\username (it may have more values separated by white spaces, but the first one must be the domain\username).
•Configure the cookie's path value to "/" (the root path). If the external application uses a different path, the lower hierarchy of that path must host both Bizagi and the external application.
•If the external application uses a different version of the .NET framework than Bizagi, the following property must be included to the machine key:
compatibilityMode = "Framework20SP1, for example:
<machineKey validationKey="478..." decryptionKey="317..." validation="SHA1" compatibilityMode="Framework20SP1" />
•Bizagi expects the cookie in the following format:
[Cookie_name]: value=[Encrypted_Data]; Expires=[Expiration_date_UTC];
So the external system should generate the cookie in the same format. If it is not possible, Bizagi also accepts the cookie in this format:
[Cookie_name]: [Encrypted_Data];
|
You should take some security precautions when establishing a path in an authentication cookie with the value / or when using a shared one between several applications. All applications receive and process the same cookies, and if they have the same Machine key in their configuration, these applications can decrypt the cookie, modify it or change the authenticated user, thus creating a security breach in Bizagi if one of the external applications mishandles the cookie. We strongly recommend that you only use Form Authentication with trusted applications, and always consider the risks of sharing your authentication cookies. |
Last Updated 1/31/2023 11:30:41 AM