Overview
Single Sign-On (SSO) setup requires some elements that demand some maintenance tasks, so you keep on going your system. When you are using OAuth authentication protocol, you must keep track of the authentication keys that expire. Depending on the application you are integrating with an IdP using OAuth, you must perform one of the maintenance tasks described below.
Authentication maintenance tasks for the Customer Portal and cloud-based portals
When configuring the Customer Portal and cloud-based portals to integrate with an IdP using OAuth, you must generate a Client secret whose value must be updated in the Customer Portal. This Client secret also has a expiration date and its your responsibility to keep track of it. For example, if you are using Azure AD as your IdP, you can verify the Client Secret's expiration date in the Azure AD portal.
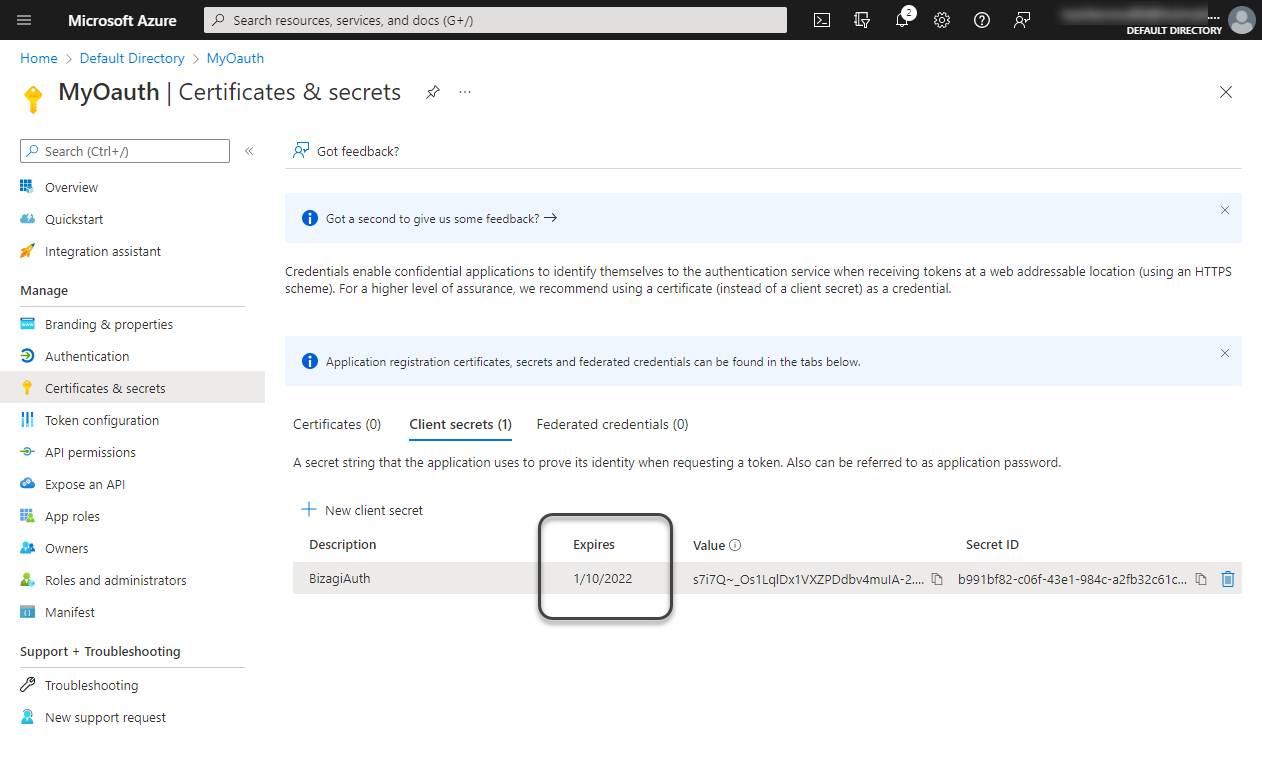
Before the Client secret expiration, you must generate a new one. Then, go to the Customer Portal's settings and, in the Security options, select Authentication Protocols. Look for the authenticator that is using OAuth as the authentication protocol (in the Customer Portal it appears as Open ID Connect) and update the new Client Secret's value in the corresponding option to conclude the maintenance task.
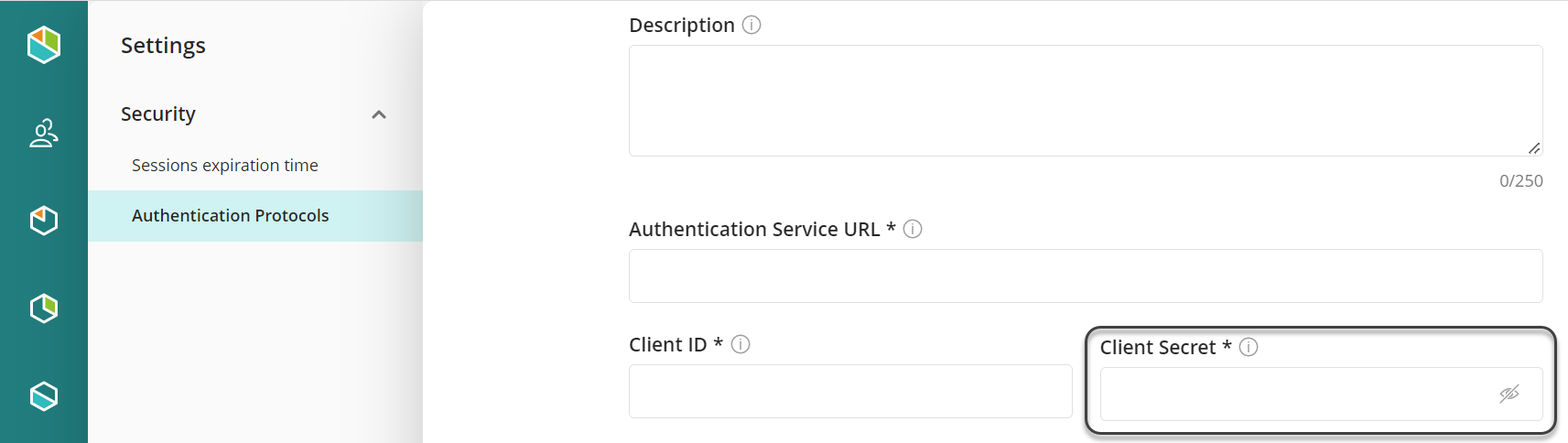
Authentication maintenance tasks for the Work Portal
For the authentication of the Work Portal using OAuth, you must create a Client secret that must be registered in Bizagi (either Bizagi Studio or the Management Console). This Client secret also has a expiration date and its your responsibility to keep track of it.

Before the Client secret expiration, you must generate a new one and update its value in Bizagi's authentication configuration (either Bizagi Studio or the Management Console), thus concluding the maintenance task.
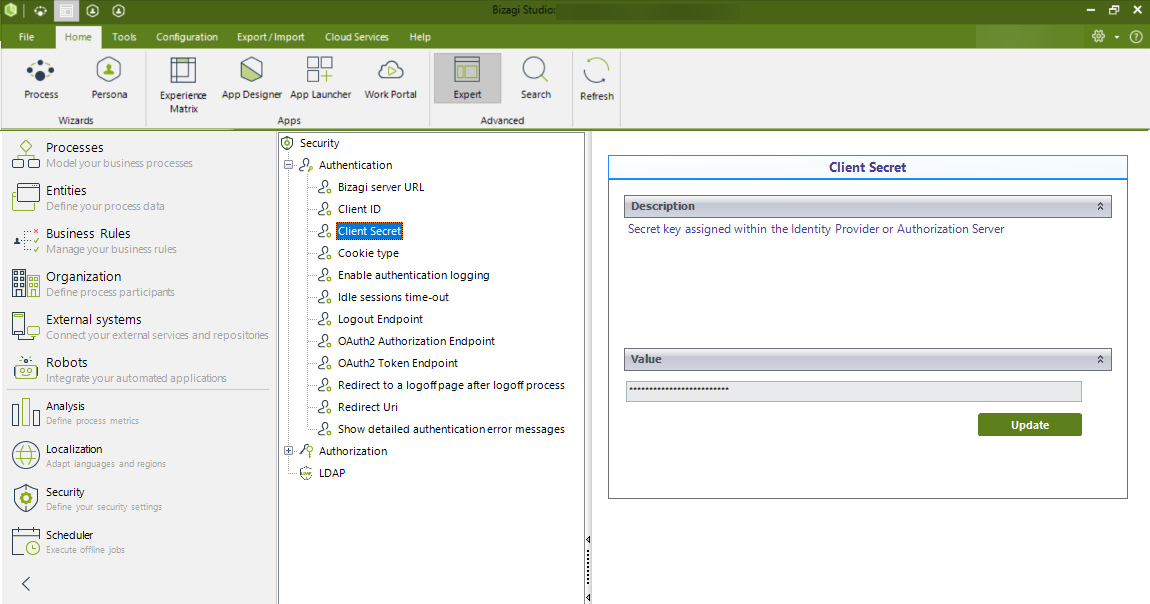
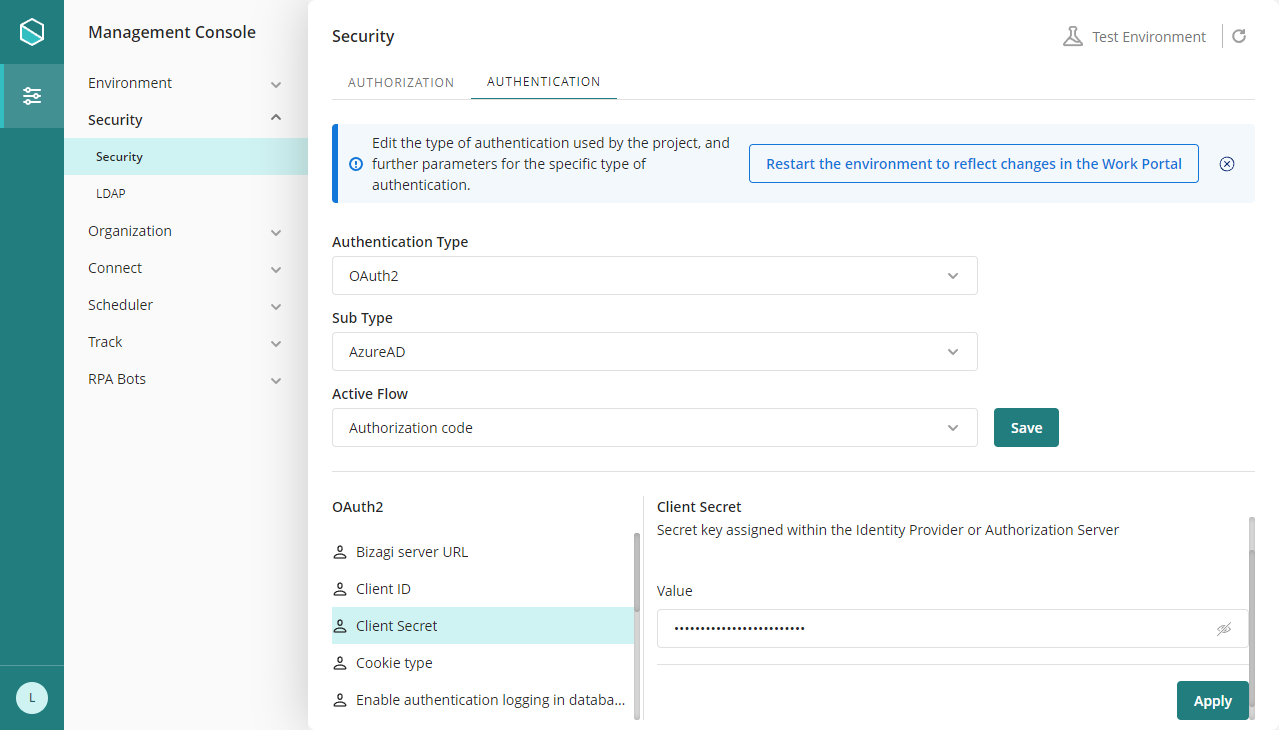
|
In the management console, before modifying the authentication configurations, it is necessary to set the environment status as Maintenance from the maintenance window. After doing the desired modifications, remember to restart the environment to reflect the changes. |
Last Updated 1/10/2025 9:17:59 AM