Overview
Bizagi Authentication is the authentication type set by default in Bizagi projects.
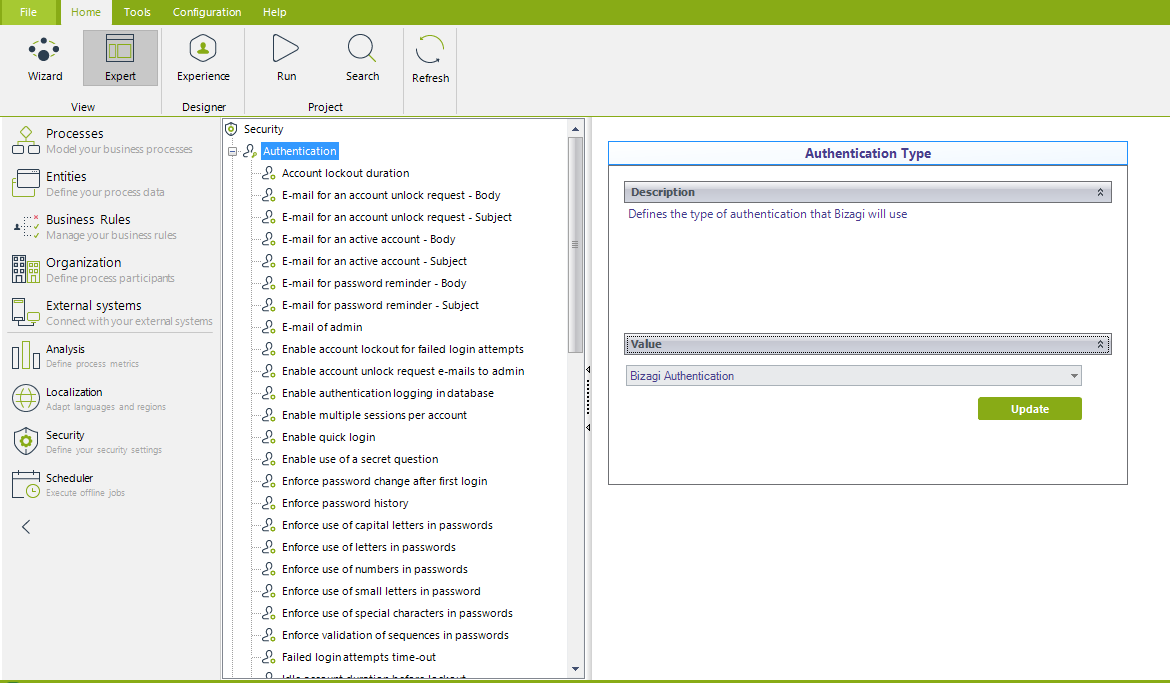
When using Bizagi Authentication, stored passwords use a SHA-512 hashing algorithm.
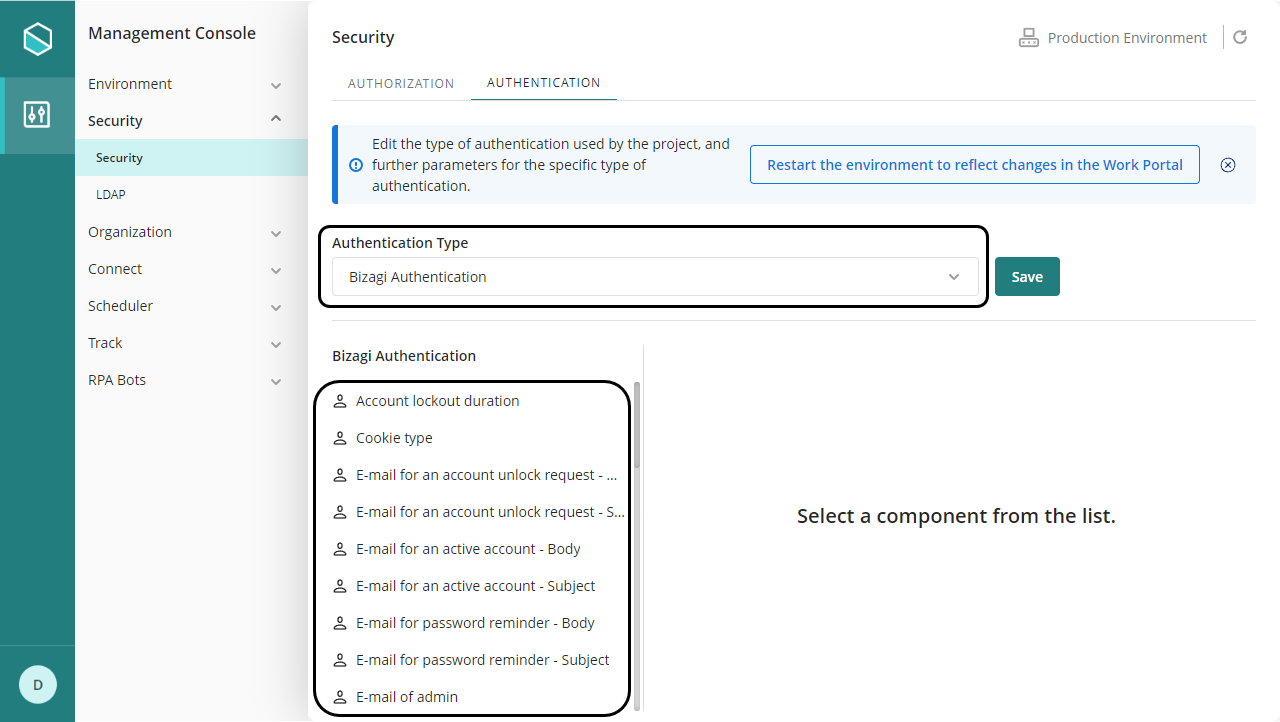
You can also set or change these parameters from the Management Console.
|
In the management console, before modifying the authentication configurations, it is necessary to set the environment status as Maintenance from the Maintenance window. After doing the desired modifications, remember to restart the environment to reflect the changes. |
With Bizagi Authentication chosen, there are additional options and parameters displayed to allow configuring the explicit behavior for users sessions and their administration, such as a longer session time, number of concurrent sessions per account, password expiration time, amongst others:
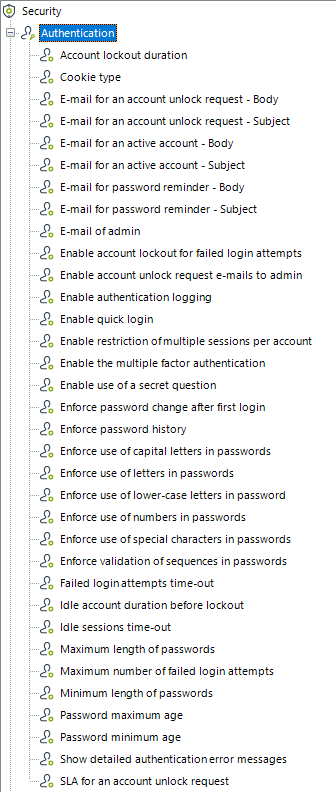
The following table presents the options to set, optimize and customize the parameters for user administration and authentication at the Work Portal:
Option |
Description |
|---|---|
Account lockout duration |
Defines the number of minutes an account remains locked out due to reaching Maximum number of failed login attempts (and having set Enable account lockout for failed login attempts), before automatically being unlocked. This duration must be greater or equal than Failed login attempts time-out. |
Cookie type |
Defines whether Bizagi uses Persistent o Session cookies. The idle session time-out defines the expiration time for cookies. |
E-mail for an account unlock request - Body |
Defines the body of the mail to be sent to the administrator when a user requests the unlocking of an account (i.e when using Enable account unlock request e-mails to admin and specifying E-mail of admin). Use with E-mail for an account unlock request - Subject. |
E-mail for an account unlock request - Subject |
Defines the subject of the mail to be sent to the administrator when a user requests the unlocking of an account (i.e when using Enable account unlock request e-mails to admin and specifying E-mail of admin). Use with E-mail for an account unlock request - Body. |
E-mail for an active account - Body |
Defines the body of the mail to be sent to a user when his/her account is created and set as active. Use with E-mail for an active account - Subject. |
E-mail for an active account - Subject |
Defines the subject of the mail to be sent to a user when his/her account is created and set as active. Use with E-mail for an active account - Body. |
E-mail for password reminder - Body |
Defines the body of the mail to be sent when the user requests a password reminder. Use with E-mail for password reminder - Subject. |
E-mail for password reminder - Subject |
Defines the subject of the mail to be sent when the user requests a password reminder. Use with E-mail for password reminder - Body. |
E-mail of admin |
Defines the e-mail of the administrator of accounts in charge of receiving E-mail for an account unlock request (i.e when using Enable account unlock request e-mails to admin). |
Enable account lockout for failed login attempts |
Establishes if accounts should be locked out when a maximum number of failed login attempts is reached (to use with Maximum number of failed login attempts). |
Enable account unlock request e-mails to admin |
Establishes if e-mails are sent when a user requests an account unlock. Use with E-mail for an account unlock request, and E-mail of admin. |
Enable authentication logging |
Establishes if an audit log is recorded with all authentication events. If enabled look for the table AUTHOLOG in the database. Notes: •Using Quick login feature does not create records in the authentication log. •Even when this option is disabled, failed authentication attempts are logged. This happens so that failed attempts can be counted and validate if the account should be blocked after a certain amount of failed attempts. |
Enable quick login |
Applies only to the Development and Test environments.
Establishes if login to the Work portal is done without inputting the passwords of accounts (a quick login through a drop-down list displaying valid login accounts). The drop-down list will show the first 100 active users (from the 101th user, accounts need to be typed into a text field). To use for unit tests or quick prototyping purposes (this setting is not valid for a production environment). When using quick login, the work portal's authentication log query feature will not record login events. |
Enable restriction of multiple sessions per account |
Establishes if more than one simultaneous session is allowed for a same account. When this option is enabled, cookies will be treated as session cookies. |
Enable multiple factor authentication |
Establishes if the project uses multiple factor authentication. |
Enable use of a secret question |
Establishes if a secret question and answer can be filled out by users, in order to have the possibility of avoiding an account lockout when the password is forgotten. |
Enable password change after the first login |
Establishes if a user must change the password after the first login. Consider using this option or setting an explicit number of days for Password minimum age. |
Enforce password history |
Defines the number of unique passwords an account must have before reusing an older one. |
Enforce use of capital letters in passwords |
Establishes if passwords must contain at least one capital letter. |
Enforce use of letters in passwords |
Establishes if passwords must contain at least one letter. Consider using Enforce use of capital letters in password and Enforce use of lowercase in password instead. |
Enforce use of numbers in passwords |
Establishes if passwords must contain at least one number. |
Enforce use of lower-case letters in passwords |
Establishes if passwords must contain at least one small letter. |
Enforce use of special characters in passwords |
Establishes if passwords must contain at least one special character (i.e non alphanumeric characters). |
Enforce validation of sequences in passwords |
Establishes if passwords are not allowed to contain character sequences (e.g: abc or 12). |
Failed login attempts timeout |
Defines the number of minutes in which failed login attempts time-out. The counter that stores this number of attempts is reset after this time frame, provided that the Maximum number of failed login attempts is not reached. |
Idle account duration before lockout |
Defines the maximum number of days before an unused account is locked out (unused accounts are those which have not had activity in that time frame). |
Idle sessions timeout |
Defines the time in minutes an idle session expires, requiring re‑authentication. This also sets cookie expiration.
Bizagi recommends a maximum of 60 minutes for security. Longer values are technically possible but increase the risk of hijacking or unauthorized access. If extended, use extra safeguards such as workstation auto‑lock and re‑authentication for sensitive actions. |
Maximum length of passwords |
Defines the maximum number of characters for passwords (use zero if a maximum length is not desired). |
Maximum number of failed login attempts |
Defines a maximum number of login attempts before an account is locked out. Applies when Enable account lockout for failed login attempts is active. |
Minimum length of passwords |
Defines the minimum number of characters for passwords. |
Password maximum age |
Defines the maximum number of days in which a password can be used, before it requires to be changed (i.e, the expiration time of passwords). |
Password minimum age |
Defines the minimum number of days in which a password must be used, before it is available for a change. Consider using this option or setting an explicit number of days for Enable password change after the first login. |
SLA for an account unlock request |
Defines the expected service time (in hours) to process an account unlock request. |
Bizagi Password Policy
Bizagi has a password restriction as an extra security measure: the user's password should not contain portions from their user name.
|
When setting passwords from the Work Portal's User menu, Bizagi ignores all password policies. |
Last Updated 1/15/2026 10:31:22 AM