Overview
When integrating Bizagi with your corporate SAML 2.0-compliant Identity Provider, you may want to rely on specialized third party tools to make sure that configuration on your Identity Provider is appropriate.
For this, inspecting how SAML 2.0 messages (like tokens and assertions) are exchanged can be helpful for troubleshooting purposes.
This document illustrates how to use an extension to Mozilla Firefox to inspect and verify SAML 2.0 messages.
Before you start
You must have both your Identity Provider and your Bizagi project, set up to support HTTPS.
If you are using Automation Service (Bizagi as a cloud-based service) HTTPS support included in your default Bizagi project configuration.
You must also have setup authentication for your Bizagi project via Bizagi Studio, with all its parameters set according to your specific Identity Provider (as described at http://help.bizagi.com/bizagi-paas/en/index.html?cloud_auth_saml.htm).
Prerequisites
Install Mozilla Firefox in the machine where you will test logging into Bizagi with your integrated Identity Provider.
Add the SAML-tracer extension (a third party project with an MIT-based license; its homepage at https://github.com/UNINETT/SAML-tracer) to Firefox.
Procedure
To troubleshoot your integrated authentication setup, first open Firefox and launch the SAML-tracer extension.
You may also launch the developer tools shipped in with Firefox by clicking the F12 key to see additional details.
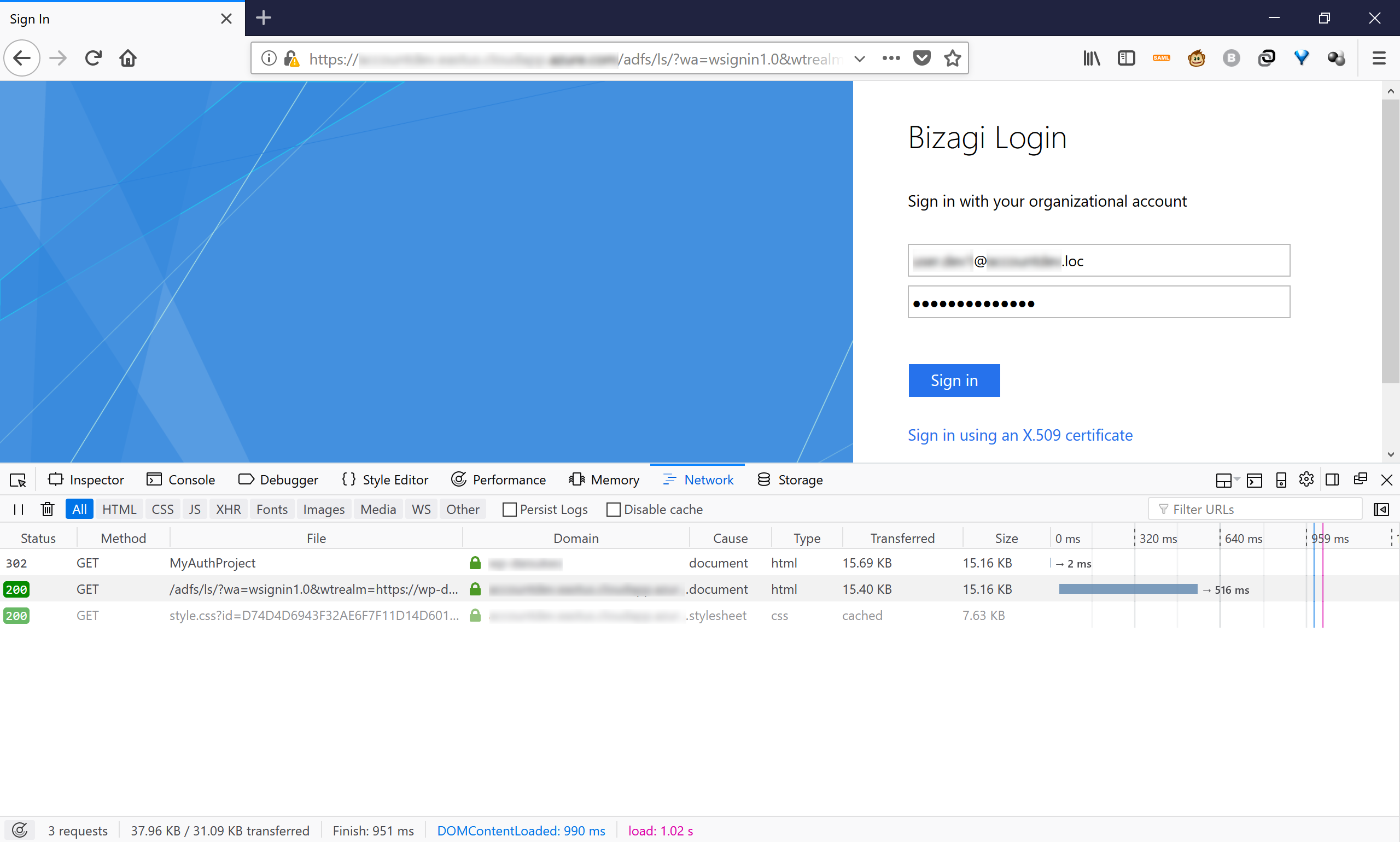
Go to the Bizagi project's URL.
Firefoxshould redirect to your Identity Provider's login page.
|
There are three types of status for assertions sent from the Identity Provide, back to Bizagi: •Responder: there was an error at the Identity Provider during the attempt to authenticate the user. •Requester: there was mismatch of information, sent inaccurately from Bizagi to the Identity Provider (a configuration issue while attempting to authenticate the user). •Success: authentication was successful on the Identity Provider's end. However, this does not guarantee that the assertion sent back to Bizagi is adequately configured (e.g., has the necessary information). |
Whenever there is a Success status, but you need to inspect how the SAML assertion is being sent, locate with SAML-tracer the POST request which has a SAML message and open the SAML tab:
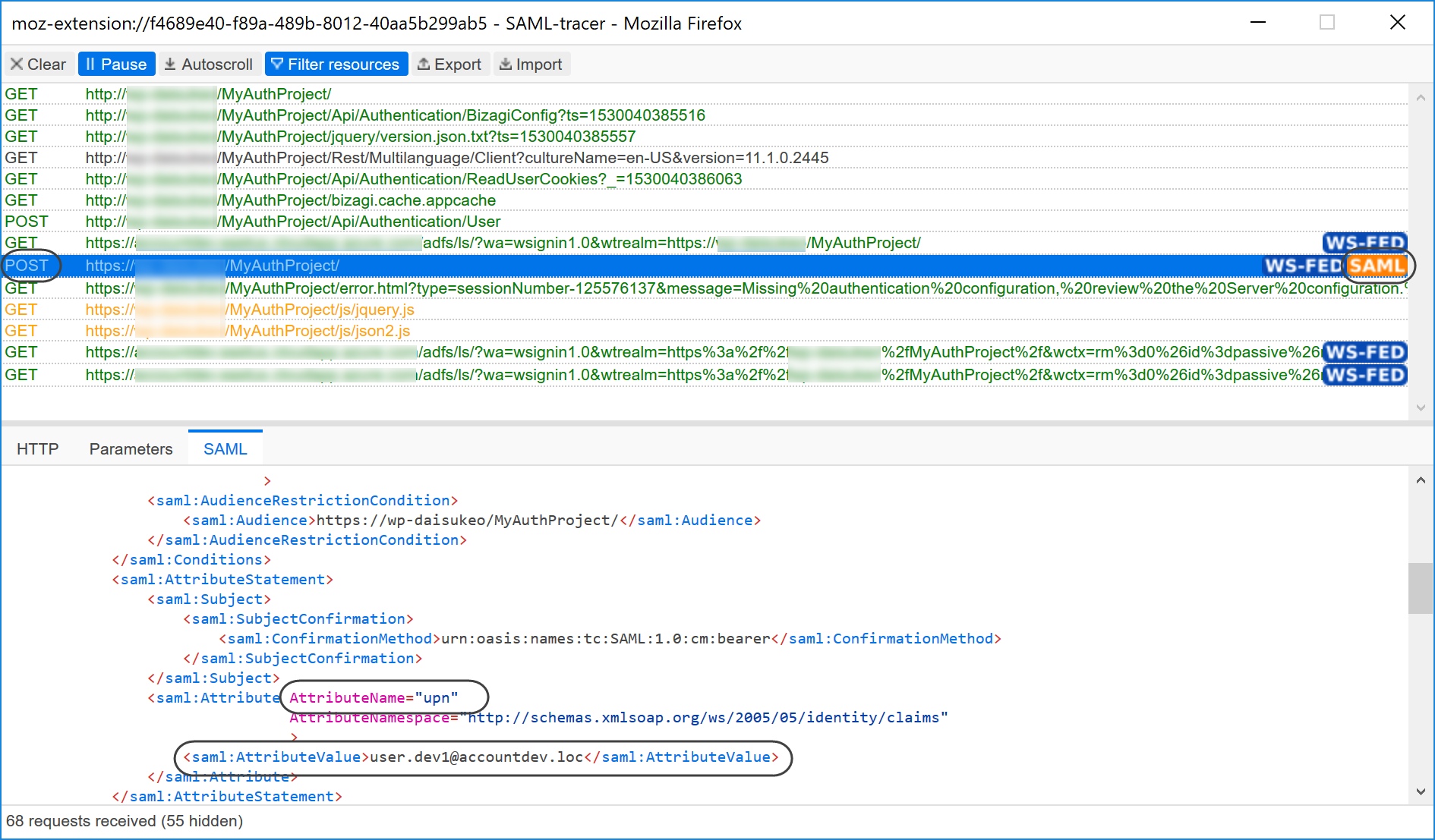
Browse for the upn attribute which is mandatory (i.e., as the Subject Id).
Its value must specify the attribute which is used for the unique identifier of a user in Bizagi.
Last Updated 7/19/2022 11:22:41 AM