|
Consider the following GDPR tips, regarding how to deliver personal data (in a machine-readable format) to individuals: •GDPR Article 20 (right to data portability) states that "The data subject shall have the right to receive the personal data concerning him or her, which he or she has provided to a controller, in a structured, commonly used and machine-readable format...". |
Note that individuals may at any time, request that their personal data as managed by you, is delivered to them.
Consider that specifically for end users, Bizagi offers an admin option at the Work Portal.
This means that an end user may request to an admin that his/her personal data is provided.
To use, first the admin relies on the user management menu options and searches for a given user.
Then by clicking on the "Download" icon, a JSON-formatted file is downloaded with personal data related to this specific user:
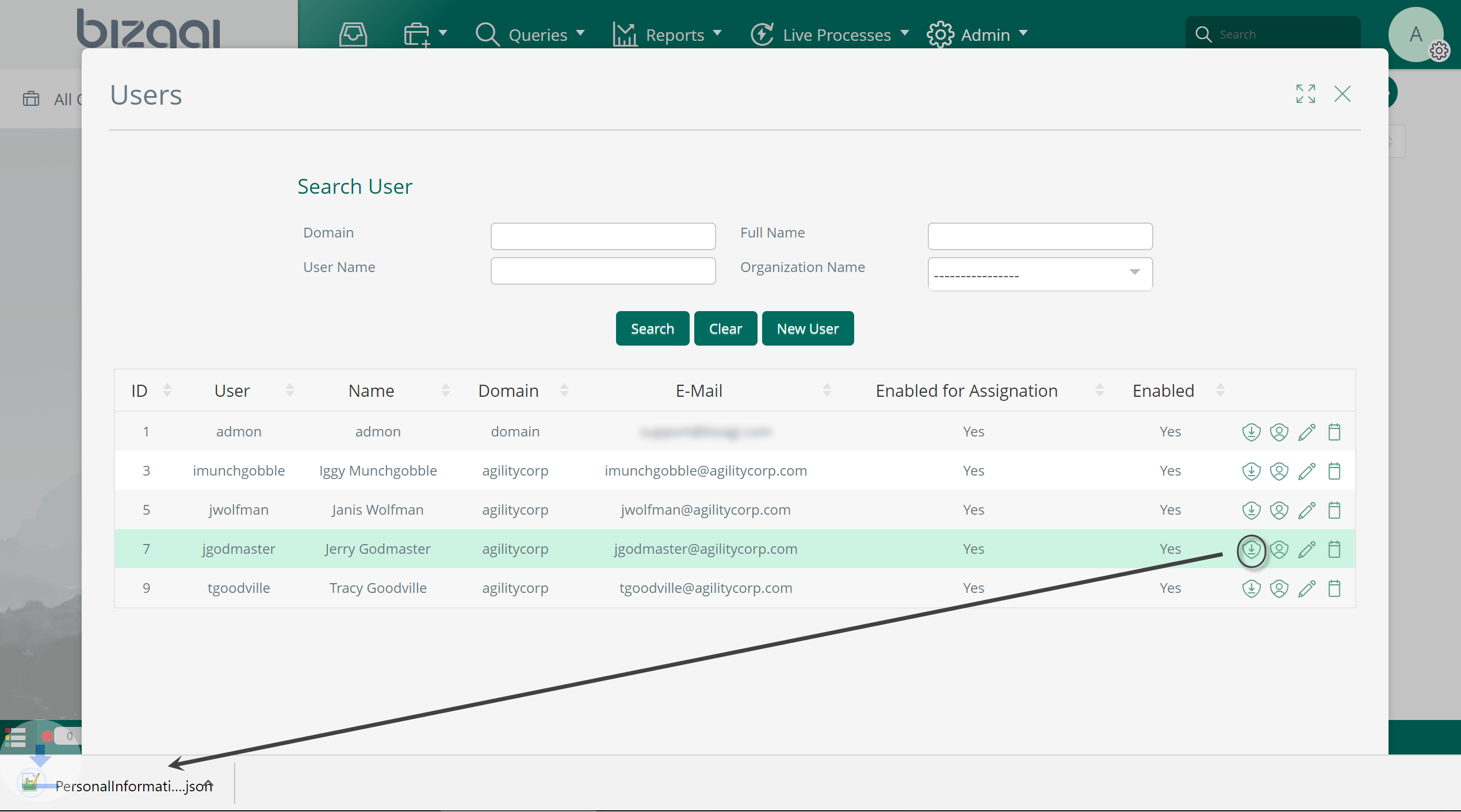
Consider that even though this option is available to admins, each end user may also do this by himself/herself as well by using the privacy menu option:
Conclusion
To comply to such requirement, the recommended strategy is to design a separate process in Bizagi that provides that possibility for individuals to get a report on their personal data.
Note that you should consider where the information of your individual is stored; given that it will not be necessarily an end user (at the WFUser), but it could also be a contractor's or vendor's contacts, customers, health care patients, etc.
Recall that you should consider that it is fundamental to have properly identified the individual and duly verified the requester's identity before delivering any personal or sensitive data.
Example
|
The following example is provided "as-is", and it simply covers the requirement whenever your individuals are end users but not other type of individuals involved in your processes (a contractor's or vendor's contacts, customers, health care patients, etc). In such later scenario, it is up to you to identify the involved entities, and implement the logic to include their information. Nonetheless the example simply highlights a base outline and it is not completely implemented (it would be further tuned and modified). |
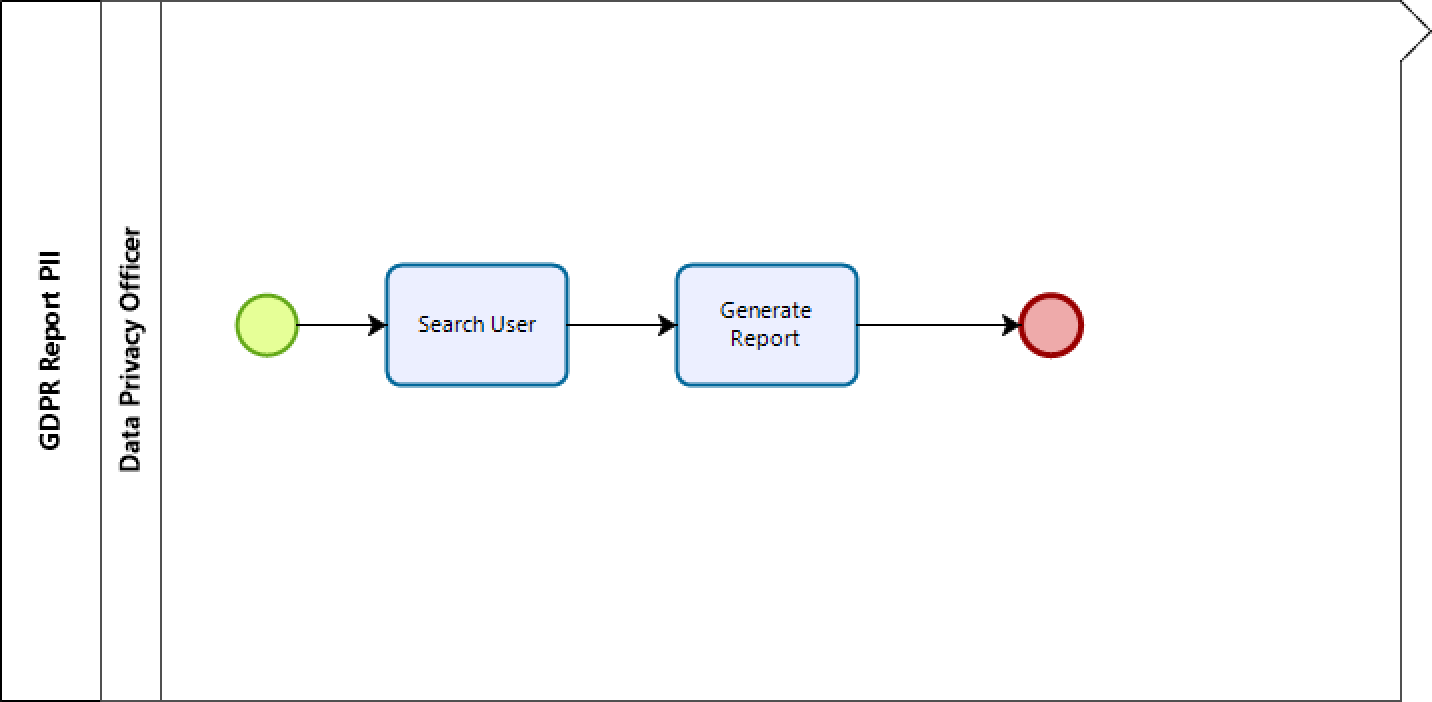
The recommended process is a simple one consisting of two activities (occurring after having verified the requester's identity):
•The first one (named Search user in the image below), having the goal to identify the individual who we want to generate the report to.
•The second one (named Generate report in the image below), having the goal of actually generating a report.
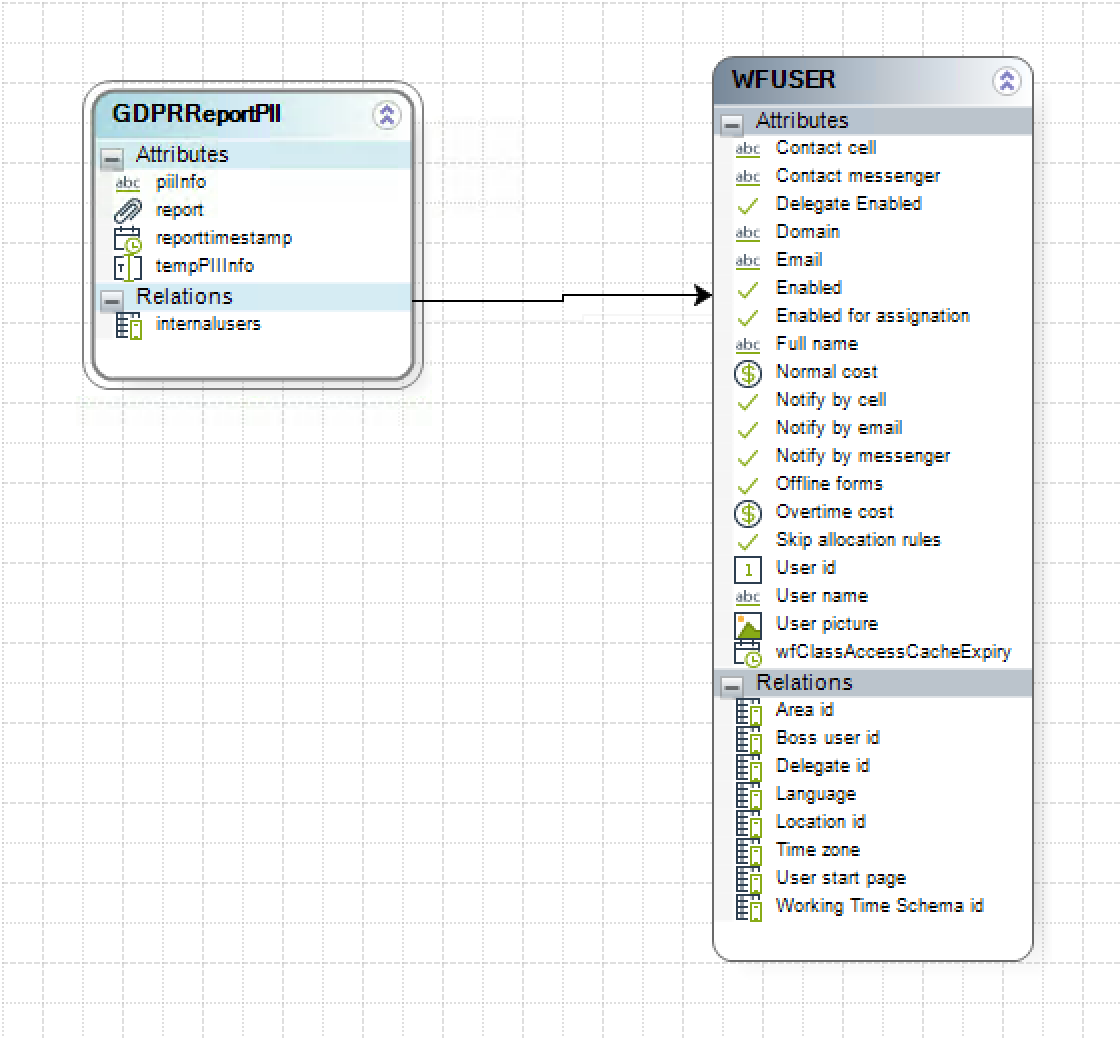
The following data model supports this sample process.
Notice that there are attributes to maintain evidence of such type of requests.
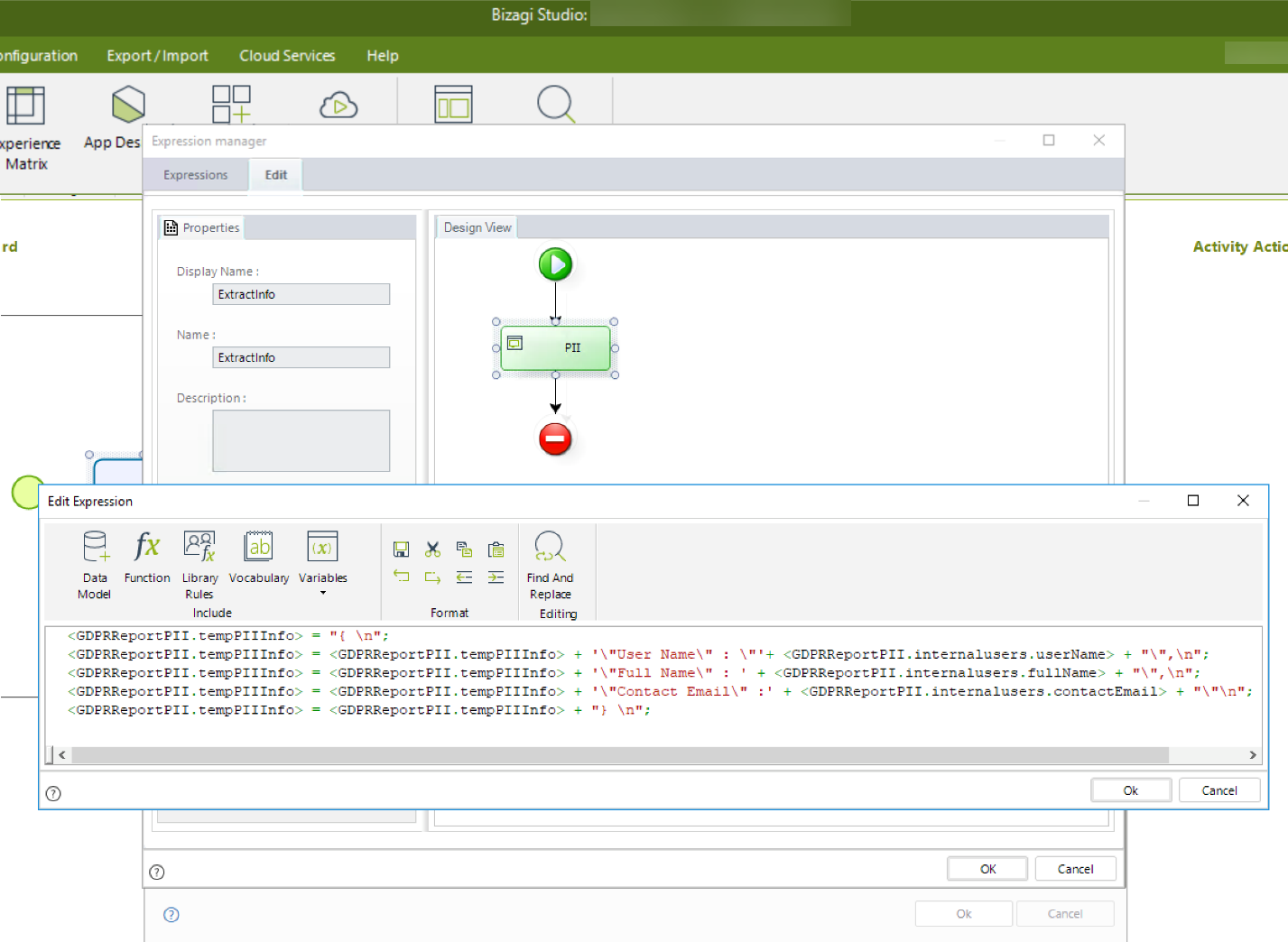
The following rule extracts personal data from the above data model (into JSON format, which is machine readable):
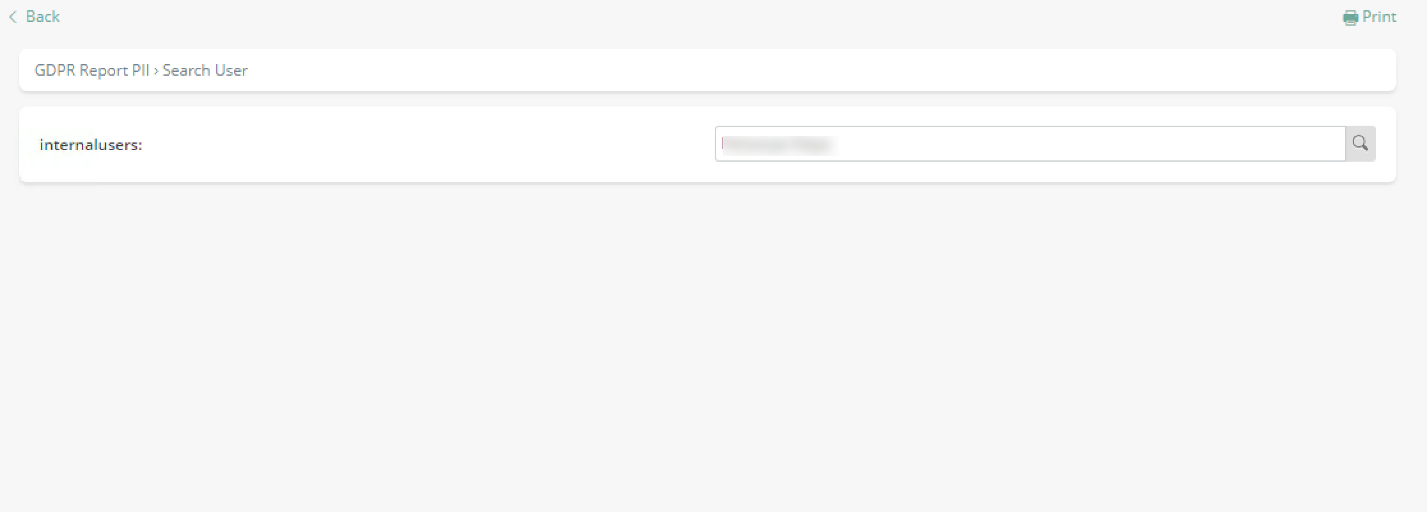
Finally and when running the process, the first activity would allow you to search for the user requesting the report.
Confirming that the user is the appropriate one would be done at clicking Next:
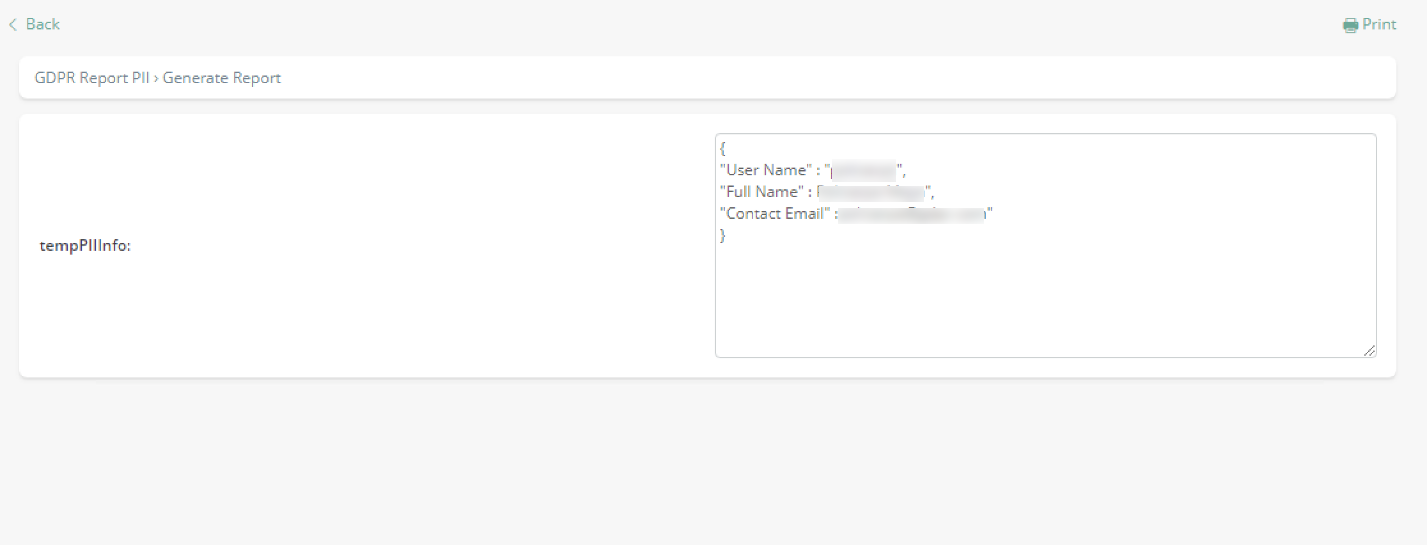
Where the second activity would show the information in a JSON format (e.g., to be copied and pasted). Recall that you may modify this example and further tune it so that the report could be, for instance, actually sent by email to the individual.
Last Updated 7/18/2023 9:29:49 AM