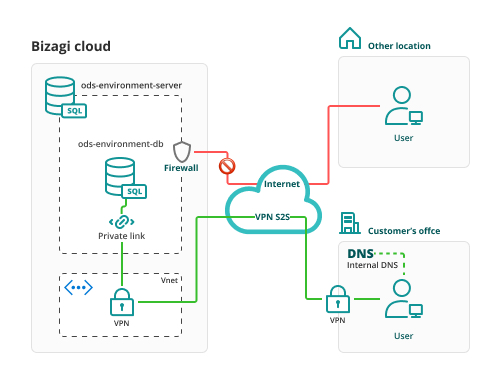
Overview
In this setup, Internet access is disabled, and access is permitted only through VPN.
All queried data by users or reporting tools within the customer's infrastructure is transmitted through the VPN; it is encrypted using TLS while in transit and is encrypted using Transparent Data Encryption (TDE) at rest.
Prerequisites for connecting to ODS
1.To connect to ODS you need an application which supports connectivity to SQL Azure databases.
We recommend using SQL Server Management Studio, with a version 18 or above (ideally latest SQL Server Management Studio).
2.Ensure your IT team can enable access to this SQL Server endpoint.
3.Allow outbound connectivity for port number 1433 using TLS 1.2 encryption.
4.Configure an internal DNS that targets the ODS database, to route data through the VPN. The DNS should target an IP and hostname sent by Bizagi. You would need to configure:[databasename].privatelink.database.windows.net
5.If you wish to enable an additional level of security, we recommend restricting IP addressed through your Firewall's policies.
6.You must configure the VPN settings to control access to your network by allowing or restricting connections as needed.
7.When connecting through Private Link, the connection could encounter a different certificate on the hostname which could cause the connection to be rejected. Therefore, you must modify the connection string to accept this certificate.
Connecting to your ODS
Make sure you securely store the credentials given that these grant access to a replica of your production environment holding your business data and Bizagi data. The steps for connecting to ODS are:
1. You will receive SQL credentials containing: Server name (i.e. [databasename].database.windows.net), DB name, Login, Password.
2. Open SQL Server Management Studio. When attempting to connect to your database server, ensure you:
a. Input Server name as provided
b. Select SQL Server Authentication
c. Specify Login and Password as provided
3. Click Options and in the Connection Properties tab, ensure you:
a. Input the DB name provided, in the Connect to database: field.
b. Tick the Encrypt connection check-box.
c. Tick Trust Server certificate check-box.
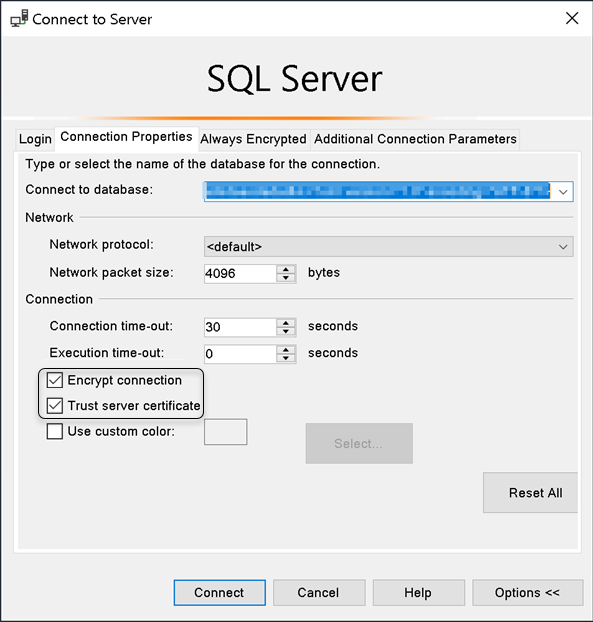
4. Click Connect when done.
5. You will be able to connect in read-only mode, and run queries using SQL Management Studio.
This service does not include query design. It is recommended to request the support of the Bizagi Professional Services team to define queries and implement best practices according to your business case.
Considerations
•A non-transactional, near real-time replica is provided (having an estimated 5 second synchronization).
•The database replica includes the information stored in the data model of the source environment. It does not include attached documents.
•The performance of the queries executed in the ODS depend on the result size. The smaller the result set, the quicker it will be. We recommend optimizing queries to return small result sets.
•If you plan to perform data-mart-style queries, we recommend offloading bulk data from the Bizagi database, load it into an external, on-premises database and make all queries there. This can be done nightly and in batches if feasible.
•The service does not replace the Disaster Recovery Service
Security
•Data in transit is encrypted using TLS.
•Data at rest in the replicated database is encrypted using Transparent Data Encryption (TDE).
Last Updated 3/4/2025 2:55:56 PM